This guide was written following a very confusing and multi-day ordeal to enumerate what was found in an instance of this software during a pen test. Hopefully this Pen Test Guide to Pentaho Business Analytics will help you if you run into it on your tests.

The summary of what this software does, is allows you to connect databases and visualize, change, and analyze the data on them. I’ve seen this used to pull sql queries, clean databases, etc. You can think of it as an automation tool for databases and their analytics.
Getting access to the tool: (Pray for default credentials/settings):

OK now that we’re past the summary.. if you see a login prompt above on port 8080, you may also see the ability to login as an evaluator with either “Admin” or “Suzy”. I love how this software gives us the default logins for us, man how nice of them. Give those a shot and hopefully at least one or both accounts will get you in. If not, you can keep guessing logins as there doesn’t appear to be a rate limit. Keep in mind that the login prompt doesn’t seem to really change when you do an incorrect password but will “suddenly” let you in once you get the right one. The caps do matter for both username and password. In our case only Suzy let us in.
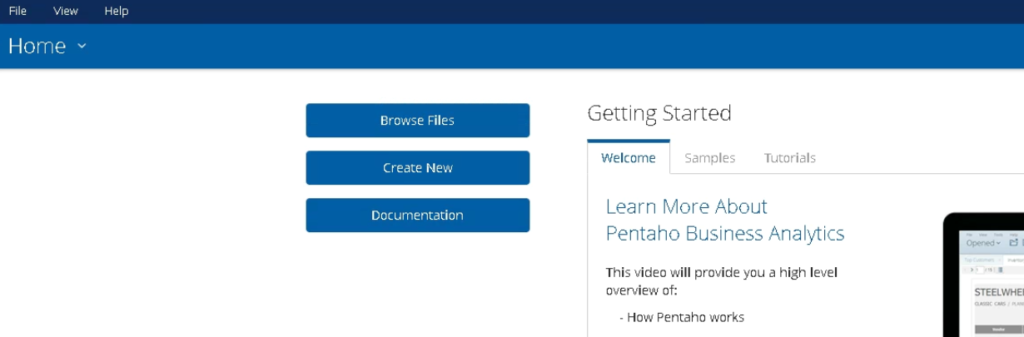
Next step you’ll see the ability to “browse files” or “create files”. In our case only the browse files capability was working so we clicked there.

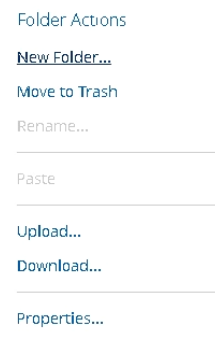
At this point, we see a bunch of options including one to download files. This wasn’t working inherently so we actually had to copy and paste files into our folder (suzy, which is now lowercase for some reason?). Once the files were in there we were able to download and view them as .ktr.
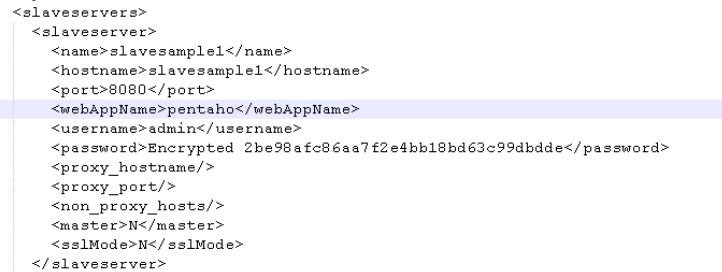
Pretty much all of the files had a “.ktr” suffix and the first thing I noticed was some hashes. These are actually other Pentaho servers and if you can crack them you get access to other Pentaho instances, nice.
If you scroll down on some of the .ktr files you’ll find a “connection” section that allows for defining connections to external databases, this is really where we get lateral movement from these Pentaho servers. You’ll see something like the excerpt below:
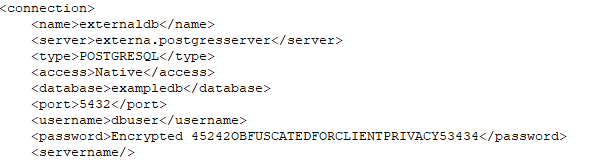
Let’s go about decrypting these passwords.. by digging into the code to see if it’s possible:
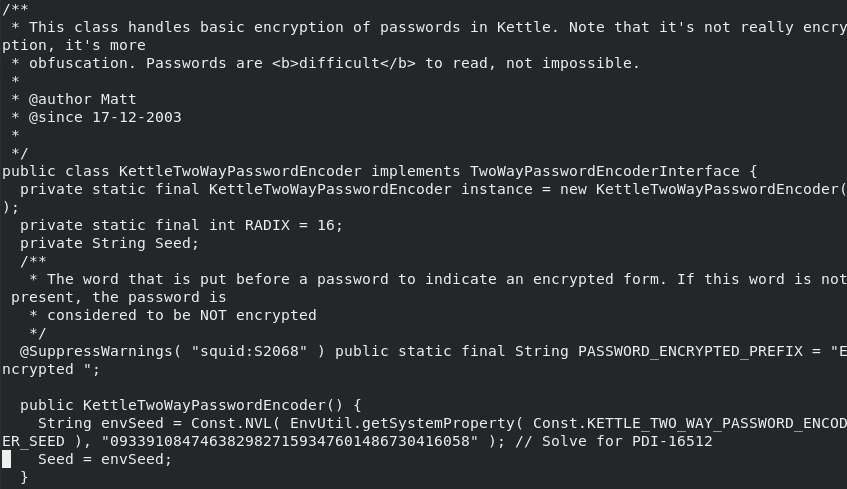
We analyzed the java code here and it turns out these are not actually encrypted, they’re just obfuscated utilizing XOR with some default seed values. Googling around we can find a guide to decrypt these passwords using a different program made by the same company called Pentaho Data Integration.
Guide to Decode Encrypted Pentaho Business Analytics Hashes:
Key Note: You are now going to decrypt these hashes in a different tool called “Pentaho Data Integration” which we will download and install.
We decided to install this on Ubuntu, first by grabbing .ktr file from this repo, then following the guide to install it here, which we will summarize the shortened version below:
1. check java and make sure its 1.8.x
java-version
2. If not, run this command to install it
sudo apt install openjdk-8-jdk
3. Next install java runtime environment as well
sudo apt install default-jre
4. Download the tool from sourceforge here. Tip: you can wget the direct link.
5. Unzip and you should see spoon.sh above, it’s already executable so just open a terminal in the folder and run:
./spoon.sh
6. You should see some sort of window that looks like this popup:
7. Right click “Transformations” and add a new transformation:
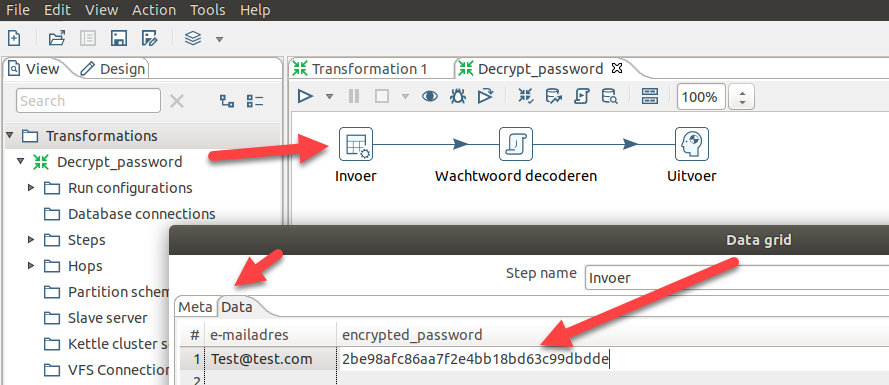
8. Drag in the .ktr file you downloaded earlier from here. You should see an “Invoer” option, double click that and press on the “Data” tab, and put in your hash under the second column. Then press OK then the play button, then “run”, and then “yes”.
9. Now… you should see some checkmarks. Click on “Uitvoer” to highlight it. Now press on the “Preview Data” tab, and you should see your decrypted password under the third column!
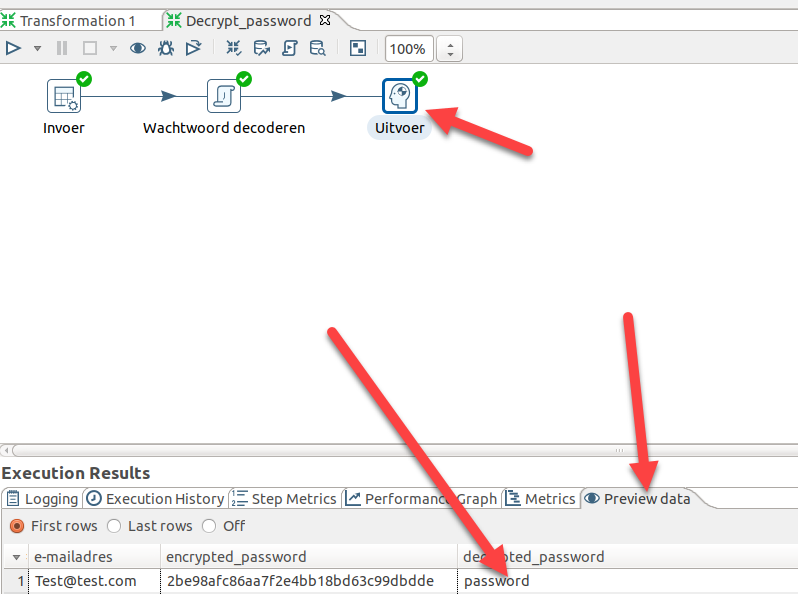
There you go!! Hash has been decrypted as “password”. Repeat for all the hashes you find!
That’s pretty much as far as we go with this Pen Test Guide to Pentaho Business Analytics. Hopefully it saves you some time from trying to analyze and recompile java scripts, failing, then just installing the software like we did :). We also did the standard searchsploit/metasploit/exploitdb search on Pentaho and only found old exploits on ancient versions of the software so this was really the only path in we found. Let us know if you have other related findings for this software!
If you found this interesting or really want to get started in pen testing, the OSCP was an excellent exam that taught me pretty much everything I know and was a great way to jump into the industry. We have a write-up for the exam here.

Dies ist nämlich klasse, Danke schön! Das hat mir gefallen und ist
ungemein wissenswert. Die Ideenfinde ich nachzuvollziehen. Solche Eingebungen sind mir gleichfalls sehr wohl durch den Kopf gegangen. Denn ich überlege, dass
das auch zum Besten von meinen Viellesern ein spannendes Thema vorzeigt.