This is a writeup for the Poison machine on hackthebox.eu which was retired on 9/8/18!
Enumeration first!
We do a standard scan with nmap:
nmap -sC -sV -Pn 10.10.10.84
We find ports 22 and 80 open, nice.
We go to 10.10.10.84.
Nice it actually lists out the files that are there.. don’t even have to gobuster!
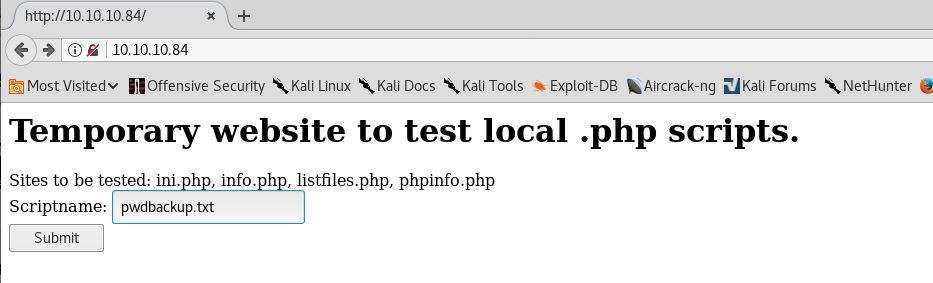
type in listfiles.php

we find pwdbackup.txt.. let’s see what that gives us
we go back to the first page and put that in and we get this:
This password is secure, it's encoded atleast 13 times.. what could go wrong really.. Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo=
Let’s decode it with base64 13 times using this resource (our favorite tool):
https://gchq.github.io/CyberChef/
the result: Charix!2#4%6&8(0
Go back, find that ssh is open so try to login with charix as user since he made the machine
ssh -l charix 10.10.10.84
Asks for password, and we’re in!
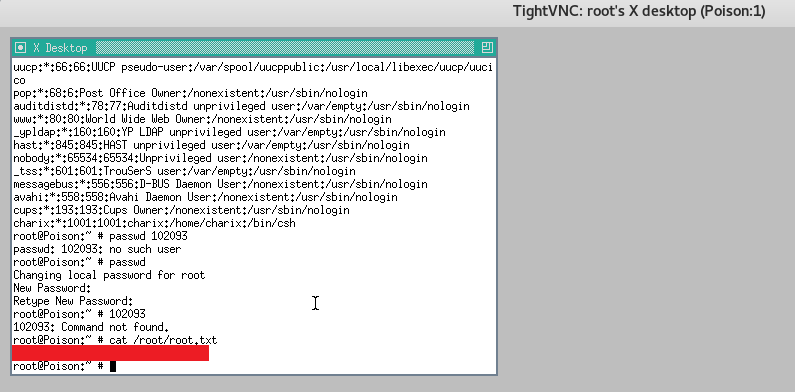
ls to find user.txt, cat that and user has been owned.
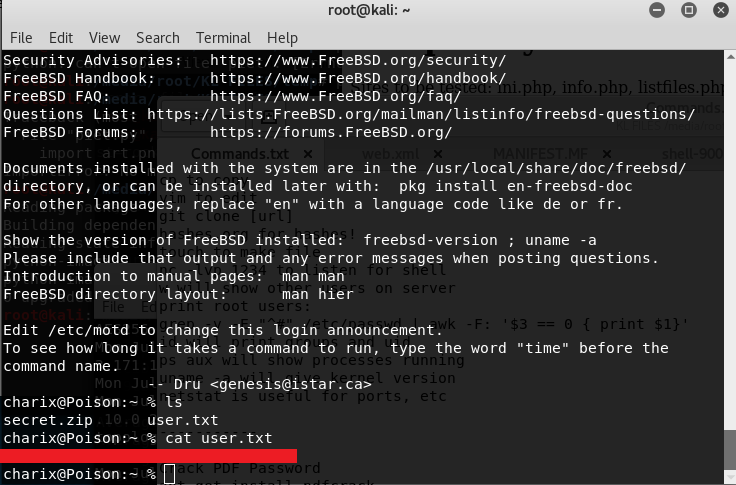
Now onto root!
let’s download the secret.zip via SCP since we have SSL:
scp charix@10.10.10.84:secret.zip /
unlock it with the password Charix!2#4%6&8(0 and leave it there for now since we can’t decipher the format.

type in sockstat -4 -l to find what ports are open and listening, we see VNC!
Since root is only listening to 5901 on 127.0.0.1, we need to do some forwarding through SSH to get there.
We found a nice guide on this here by googling vnc over ssh:
https://www.cl.cam.ac.uk/research/dtg/attarchive/vnc/sshvnc.html
Now we type the following command to make a tunnel on our kali machine:
ssh -L 5901:localhost:5901 -N -f -l charix 10.10.10.84
let’s paste the secret file we found earlier into a folder, and run the following command in a terminal
vncviewer -passwd secret
type localhost:5901 as the server
viola! we have root: