Just passed my OSCP this weekend, successfully hacking into all five boxes that were presented!
Summary of exam:
This exam is a great way to prove your penetration testing skills and a great one to add to your resume. It is a 24-hour exam (although you don’t need to use the whole time) and it is proctored, but you can do it sitting at home in your PJs. You have to get 70 points to pass, out of a possible 100. There is partial credit for owning “part” of a box, which is getting only user-level privilege and not root. There is also 5 points of extra credit for doing the lab-work and the course-work.
How I studied:
First, some background about me. I had my CEH, SEC+ and CCNA Routing/Switching before starting the OSCP (it’s good to have some foundation to go off in networking, security, etc). I was a cyber PM, analyst, and engineer at my job.
I signed up for the labs in September, 2018, by going to the official website. I paid for the minimum option, “Penetration Testing with Kali + 30 days Lab access + OSCP Exam Certification Fee”. You have to pay for at least 30 days of lab time and the training material to even attempt the exam, so that’s what I did.

You’ll get a pdf and set of video training material, I skipped the videos and went straight for the PDF. There is a 5% extra credit if you complete all of the homework problems from the PDF and hack into 10 unique boxes, which is what I did. I actually broke into about 12 boxes to be on the safe side and ensure they are unique. This is pretty much all I had time for in my 30 days of lab time.

You can connect to the lab with openVPN, which they’ll send you a connection file to do so with. It has multiple subnets to emulate a few different environments, with plenty of servers on there for you to break into. You need to get the “proof.txt” file on each server to consider it owned. You’ll also need to have an interactive shell and run ifconfig/ipconfig while doing type/cat on the text file. Something like this:
After my 30 days were up in the lab, I went over to https://www.hackthebox.eu and just broke into as many boxes as I could. I paid for the VIP membership there, which is about $15 USD a month, but gives access to less crowded boxes.
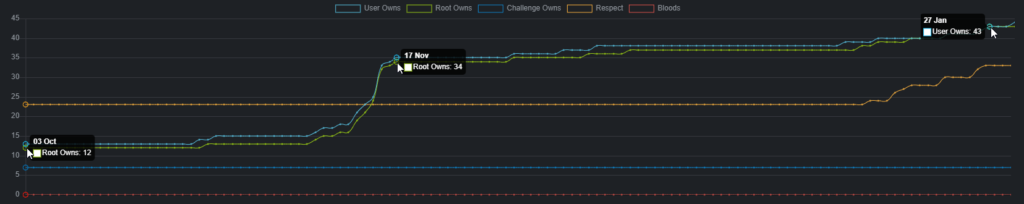
This is my box owning history on hackthebox.. graph starts in october when I joined after my OSCP labs expired, and ends in January when I passed.
First attempt:

So my first exam date was scheduled for Nov 16th. IMPORTANT NOTE: do not wait to schedule your exam, do it right when you get access.
The reason for this is that optimal start times (e.g. 10AM saturday) are really hard to book, and you often have to book them a month or two in advance. If you’re ok with a random weekday or something then you can do it with only a week or two lead time. Keep in mind you have 24 hours for the exam when you are booking.
So I had broken into about 10 or so active machines on HTB, and about 12 machines in the OSCP lab by sometime in October. By this time, I decided to practice my Windows Buffer Overflows again, and then go through about 1 or 2 retired machines a day on HTB. Retired machines have youtube videos, would highly recommend Ippsec videos like this one to learn quickly. Our blog also has quite a few tutorials on the recently retired machines. I went into the exam guns blazing… but only got about 50 of the 70 points necessary to pass. By about 22 hours in, I was beginning to take naps and just was not effective anymore. The proctors were pretty chill though, all you have to do is show them the room with the webcam, and screen share all monitors you will be using. They will note down anyone that enters and exits the room. You may take breaks and walk away, then come back at any time within the 24 hours.
So what did I do wrong? Nothing really.. although the stats aren’t published, the first time pass rate for the OSCP is probably lower than 5% from what I can determine off the internet.
Second Attempt:

So.. I failed that first exam. That’s fine, don’t let that discourage you. What I did was go straight back to HTB and continue trying to break boxes. I didn’t do any additional retired boxes, just active boxes as that emulates the OSCP the best, and I had learnt pretty much all I needed from the retired ones.
I was told that you should be able to break into most of the easy/medium ones on HTB as that’s the hardest the OSCP boxes will get, so that’s what I attempted to do.
My re-exam was $60, not a big deal, and it was to occur in late January. By the time that rolled around, I had gotten into 43 boxes total on HTB and 12 lab boxes, putting me at over 50 boxes broken into. I was feeling pretty confident going into the exam.
This time was a success! I had seen two of the boxes on my previous exam so I knocked those two out pretty quick. The next 3 weren’t too bad either so I was done with the exam in about 9 hours, including the report! I started the exam at 10AM on a Saturday and finished around dinner time, 7PM.
One other thing I want to note about the exams… the format. Aside from it being 24 hours, you’ll want to get online at least 15 mins before the exam and follow the instructions in your email. They’ll tell you how to setup the screen share and webcam share. Have your drivers license/passport ready. You’ll get a VPN connection to the exam environment and they’ll present you with a nice interface/control panel once you’ve connected, where you can reset boxes, up to 24 times during the exam (which is more than sufficient). You’ll also get access right away to a windows xp lab computer that you can test exploits on, etc (note: having access to this box doesn’t count towards your score). This is also the place to test out your buffer overflow, which will pretty much be one of your guaranteed boxes on the exam (Make sure you review the Windows BOF in the coursework). The control panel will also show you how much each box is worth if you break into the root/system level. However, it will not give you the value for just getting user/local access.
Boxes on HTB I would recommend:
These are boxes that I would recommend you do prior to taking the OSCP, with links to our write-ups if we have one for that box.
Joker (sudoedit and wildcards)
Jeeves (Pass the hash)
Waldo (Local file inclusion)
Poison (Tunneling via SSH)
Celestial (Crontab privesc)
*DISCLAIMER: I am not affiliated with Offensive Security (C) in any way, nor do I own their logos or any other trademarks. If you would like me to take any content down from this site, please contact me through the “contact us” page on this site. I have attempted to be as general as possible and not reveal anything specific about the exams, other than helpful advice that I wish I had known prior to taking them.
