If you have ever done a phishing exercise for a company, the contract probably said you have to test the creds you get. But what if they’re tokens? Are you going to manually replace them every intercept? No way, that’s extremely slow and error prone. Here’s how to automatically replace cookies in BurpSuite. In the example below, we’ll be placing the two cookies: ESTSAUTH and ESTSAUTHPERSISTENT we received during an O365 phishing request.
Step by Step Instructions for Replacing Cookies in Burpsuite
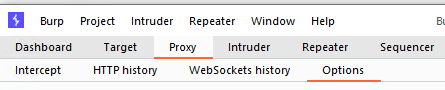
- First, navigate to “Proxy” and then “Options”:
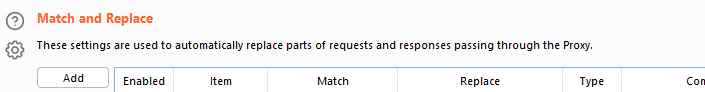
2. Next, scroll down to “Match and Replace” and press “Add”
3. For us, we want to replace all existing ESTSAUTH cookies with the one we received during our Phishing exercise, so we will use a regex match as followed:
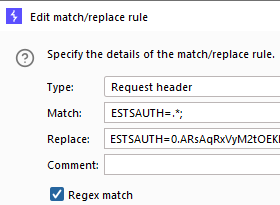
In the Match field, we put
ESTSAUTH=.*;To translate this from REGEX, this means match the exact phrase “ESTSAUTH=”, and match any amount of any character after that, and then match “;” then stop.
The replace will be our token, plus a “;” at the end, so something like this:
ESTSAUTH=0.ARsSFDGSBNVCXLKSJDFGSLKGFJCVB,.MNSDFGKLJHSDFGLKJSDFGSGSyE_azw;4. Similarly, the other cookie will look like this:
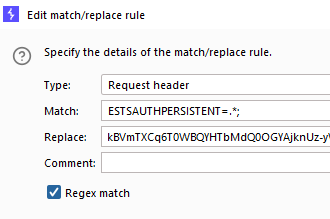
Viola – that’s how to automatically replace cookies in BurpSuite.
Summary related to ESTSAUTH and O365
In our experience, logging in with ESTSAUTH will attempt lock you in on the landing page of the phished app, especially if you’re using something in evilginx2 to capture tokens to avoid MFA. However, once you try to open anything like a document or traverse to email, you will get another login prompt prompting you to enter MFA. Just retry the URL again and with the Burp settings above in place it should just let you into email, onedrive, etc for O365.
We hope this has helped, please see our other How-To guides if you want to learn more about other cyber-related topics!

