Had a few hours this morning luckily to attend the Open Source Intelligence (OSINT) workshop presented by Brian Markham, the current Chief Information Security Officer (CISO) at EAB Global. Definitely learned a thing or two I’d love to share and also a quick write-up of the mini-Capture the Flag event (mini-CTF) we had at the end.
Google Dorking
Everyone knows google but Brian went over some tips that help with specifying google queries to do what you need em to. The main points i wrote down were:
Site: blah.com inurl:login (finds all login pages for blah.com)
Intext: blah (finds blah in the text of a page)
After: 2021/06/01 (finds pages published after a certain date – really cool)
Intitle: blah (opposite of intext, only searches titles of pages)
Useful Tools
He then went over a bunch of useful tools in detail, but here’s my chicken scratch here on what I think of them:
Yandex – alternative to google image search
Peekyou.com – useful for cross-referencing social media handles and stuff
Exiftool – good for looking at metadata in files. However, I prefer fotoforensics.com since I know the creator 🙂
Pic2map – Good for pinpointing GPS coordinates within metadata on a map, but it didn’t work for the CTF and i still prefer fotoforensics that did work for the CTF.
Familytreenow – good people and relative lookup tool. However, I prefer truepeoplesearch, but it looks like they share databases or sources to a certain degree.
Revealname – for reverse phone lookups – had to turn off adblock for this one to work, works but looks really ad-filled, I still prefer truepeoplesearch.
Carrierlookup – also for reverse phone lookups but their website appeared broken to me (couldn’t search).
hunter – professional email lookup – this one looks like rocketreach where you need to signup for a few free searches, meh.
theHarvester – really cool tool that comes with Kali to pull information about domains like ips, contacts, phone numbers from google searches, will definitely use this going forward.
whois.arin – great whois tool for looking up whole subnets
ip-netblocks – Similar to the link above
DNS Dumpster – really cool site that makes it so you don’t need to manually do reverse DNS lookups and look at historical trends.
Trufflehog – git repo search for secrets and stuff
Git-secrets – software to prevent the above from happening, heh.
Shodan

We also were taught extensively about Shodan. Can use quotes to find phrases in quotes like “Webcam XP 5” to find sites with certain phrases in the header (that one finds open webcams).
Here were some other useful queries we were taught:
Net: xx.xx.xx.xx/yy – specific CIDR block
Port: 443
Http.status: 200 – filter by response code
Org: Stanford – filter by organization the server is assigned to
Country: US – country the server is in
Mini-CTF Write-up
This was a really quick CTF that took me about an hour to complete, but really reinforced some of the topics in the class so thank you for putting it together! I will try to grey out the flags but honestly most of these you can google and get pretty quickly.
This is how I did.. had a meeting at the start otherwise I would have started earlier :(. 3rd ain’t bad though.
The CTF was focused around Brian so some of the private details I’ll try to grey out as well.
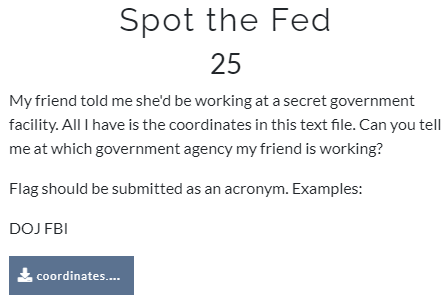
Spot the Fed
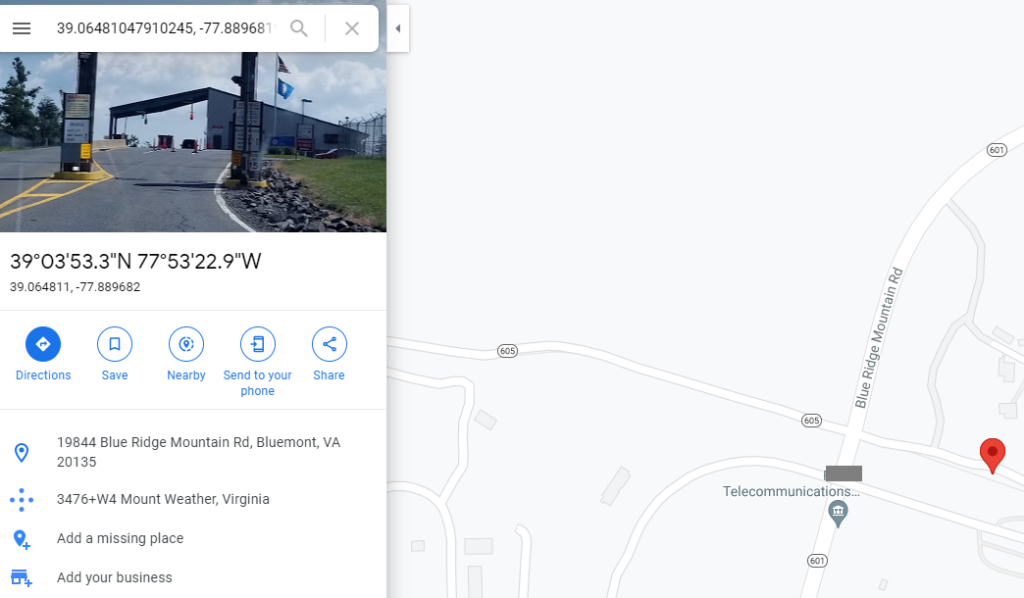
Googling the location pretty much gives you the answer, which is greyed out. You can also kind of tell by the flag in the picture and the sign at the building.
Agnes
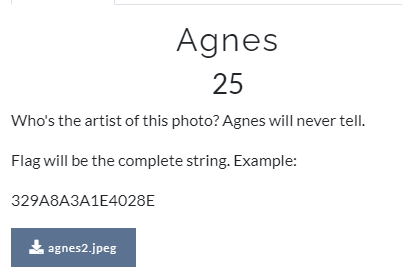
We used fotoforensics for this which gave us the answer pretty directly which was in the metadata. Could have used Exiftool too!
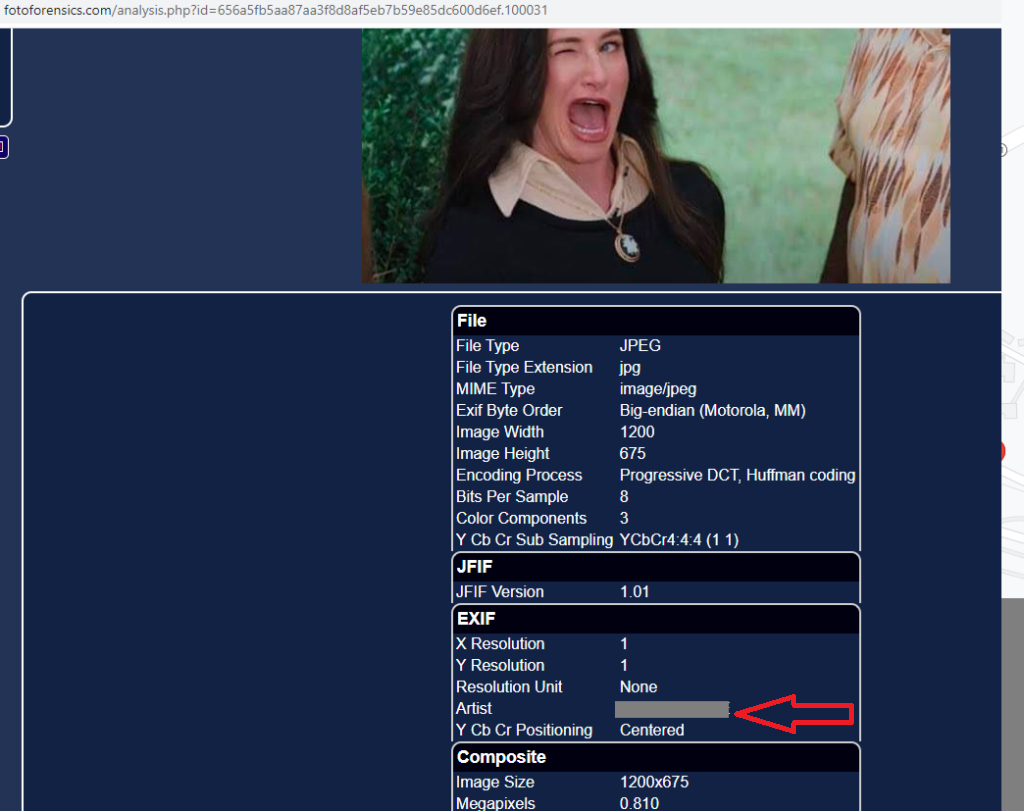
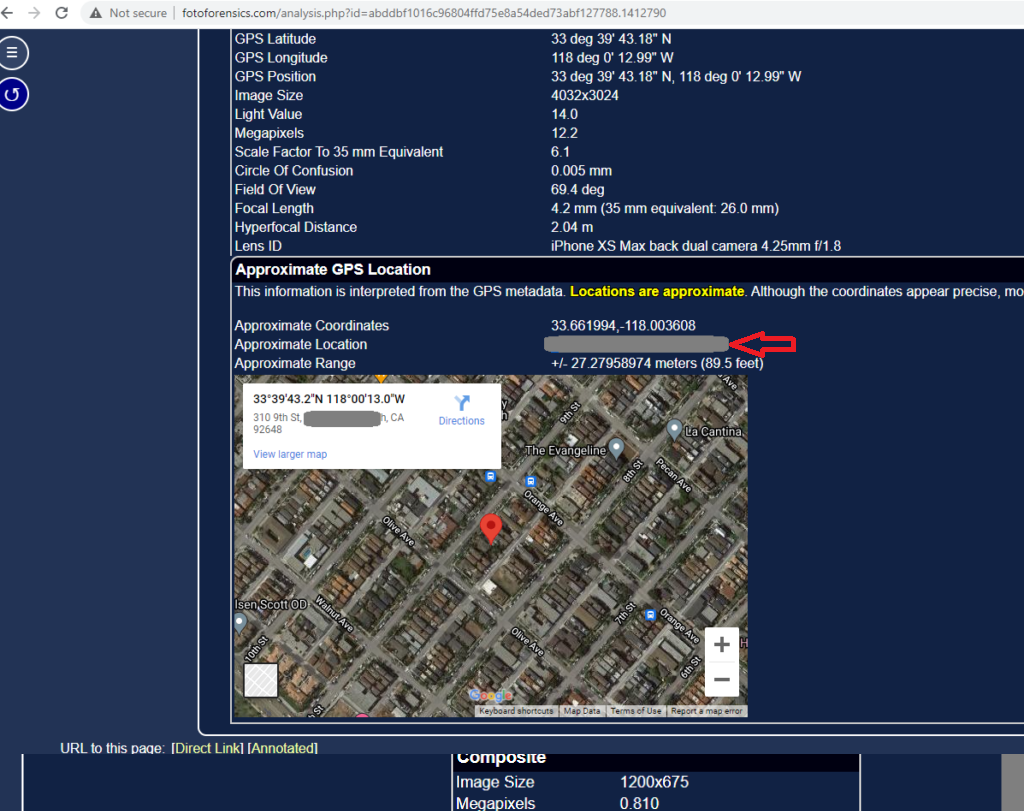
Vacation Photos
This was the picture (I stripped the metadata):

Used fotoforensics for this as well, as pic2map didn’t work for some reason:
Emergency 911
We just googled it the normal way:
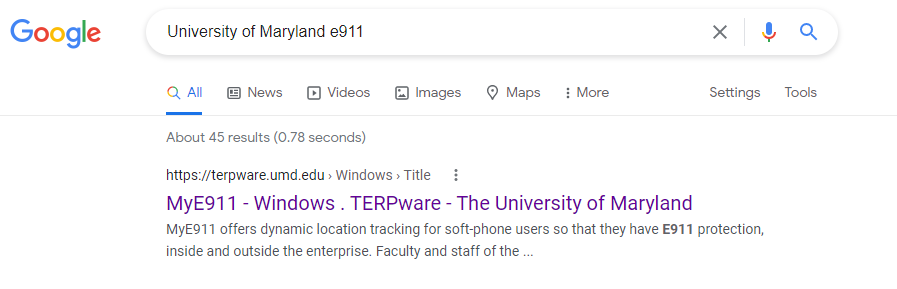
This first result had the greyed out flag:

My Pillow
No idea who this guy is (probably should know) but found his site on Wikipedia:
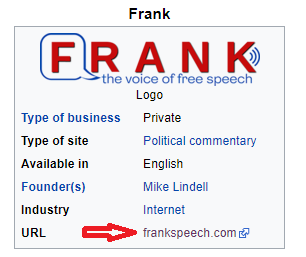
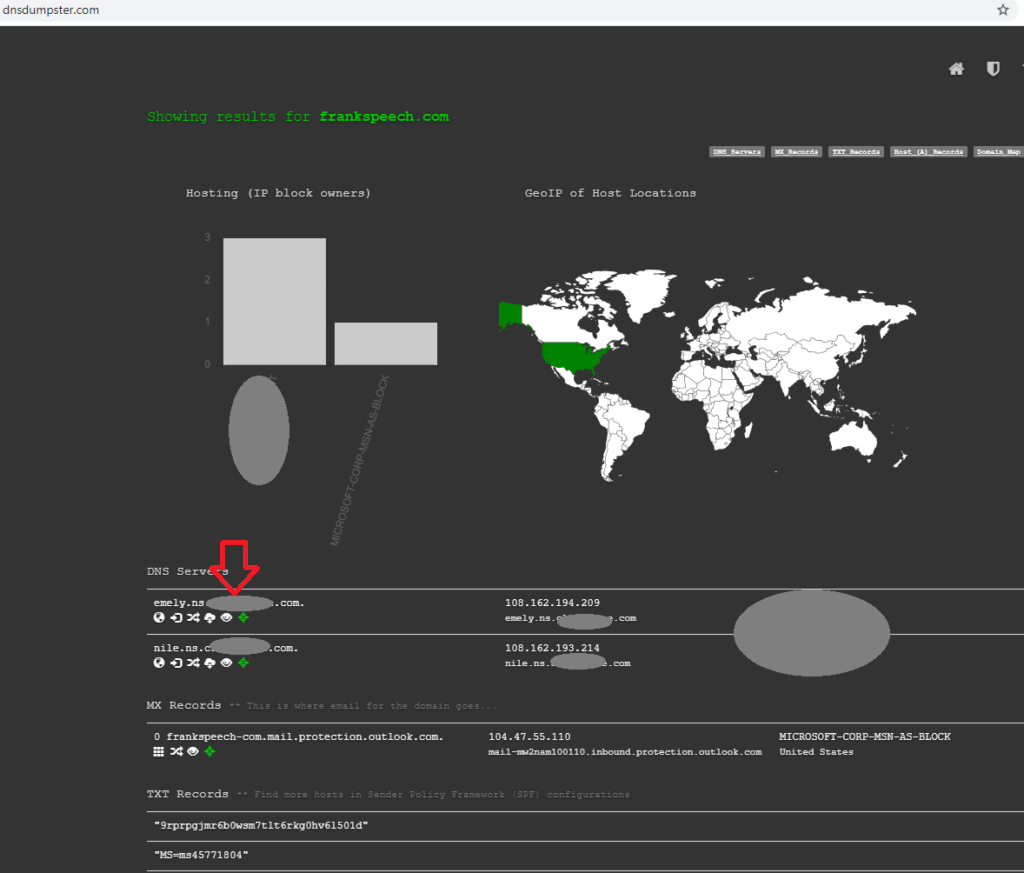
Could have done a reverse NS lookup but used dnsdumpster instead since we were just taught about it 😀
It has the company which the DNS servers are at as well, which is a major DDoS prevention vendor, but not technically sure if that counts as “hosted”. However, it would have been hard to find the true host since this vendor masks the true ip of the server, so I’m glad the DDoS prevention vendor was the right answer heh.
Mac Lab
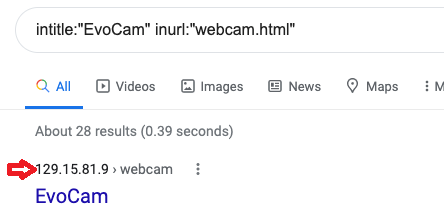
This was the screenshot:
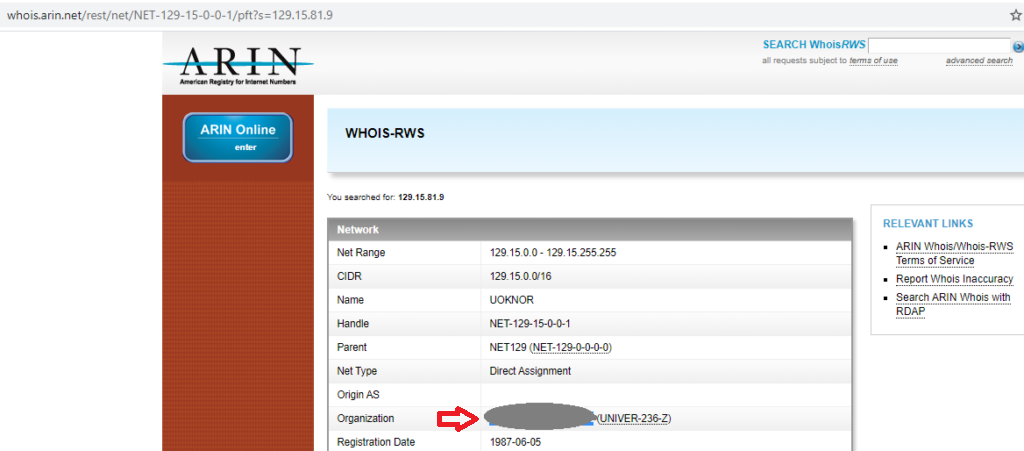
It had the IP so we just ran it through arin which was taught to us in class, and viola it has the organization!
Old Phone

Now we get to some of the harder stuff… The presentation he gave said he worked at PWC so I googled this:
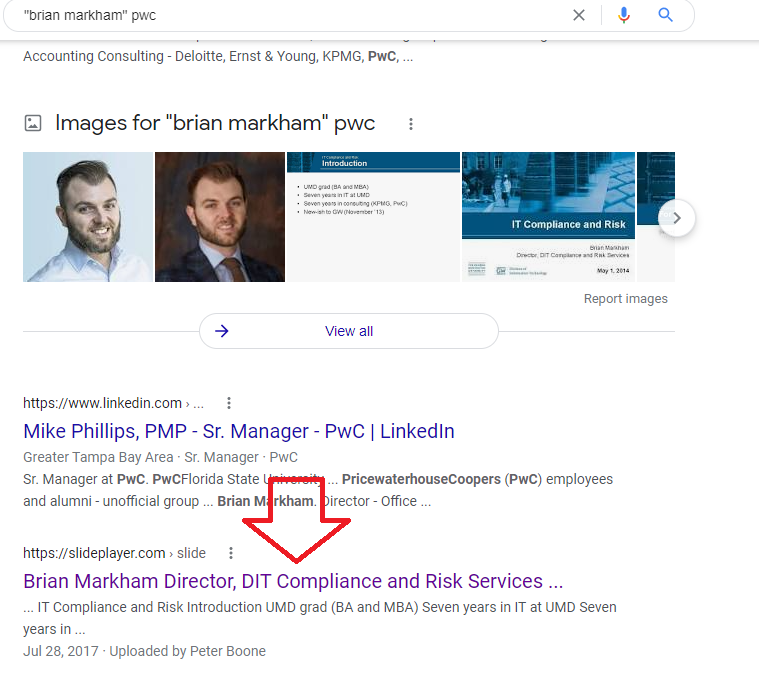
There were some slides with his number in it! yay!
Heat on Feet

This one actually had me stumped for a while. I used peekyou first to find that maria person:
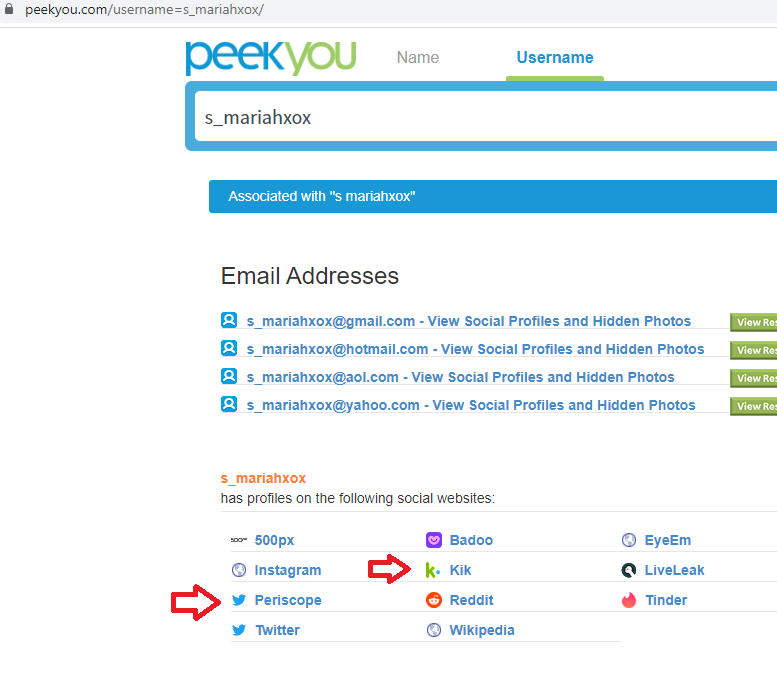
The Kik link actually gives you her real name which is Samantha or something, but the Periscope link went to another twitter which had a person based in NJ:
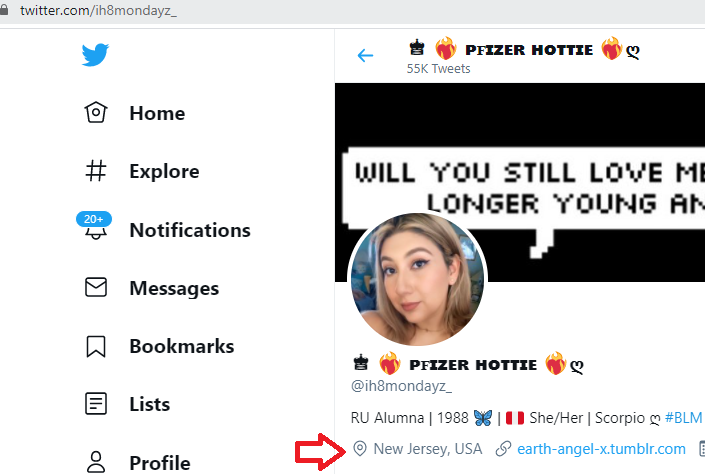
Also if you zoom in on the photo it gives the city:

So I googled it and indeed it exists:
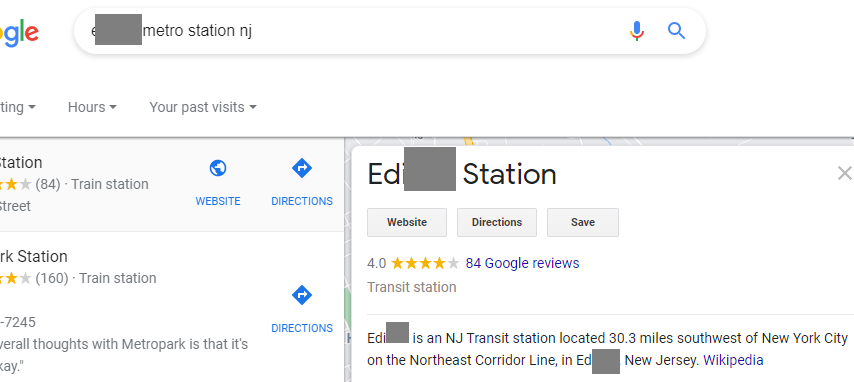
Now for the extra hard stuff:
If it pleases the court
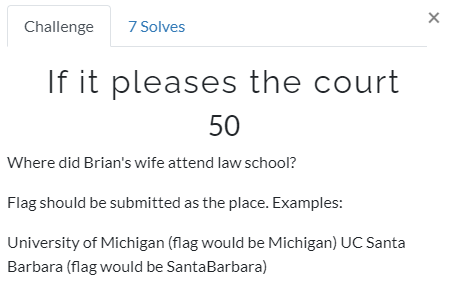
Now I typed in FamilyTreeNow and used College Park, MD since we know Brian went to school there from his presentation. We find his past addresses listed:
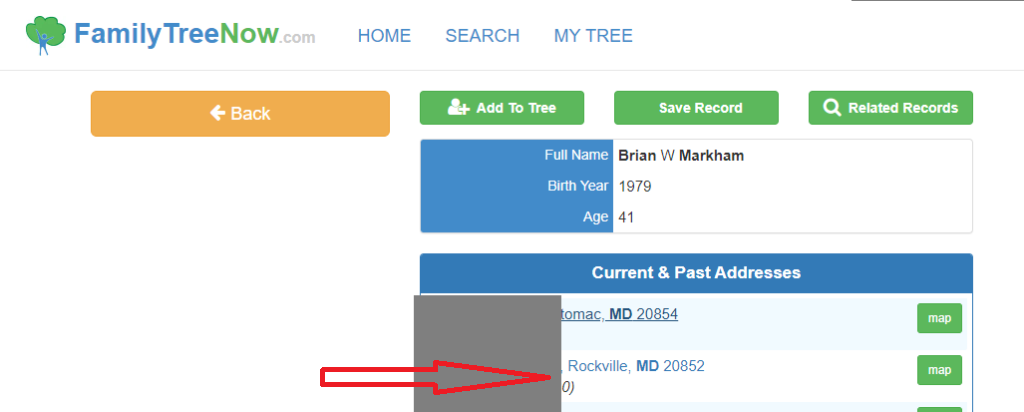
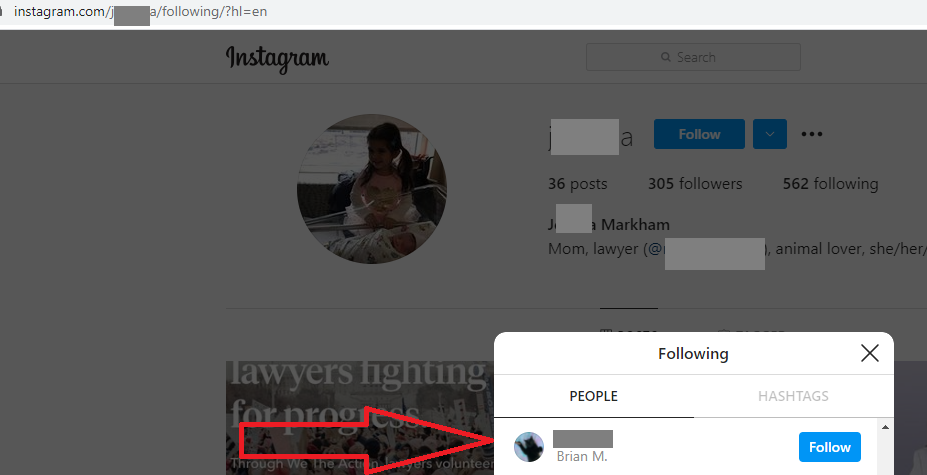
Then I was able to find the name of his wife (J____A)
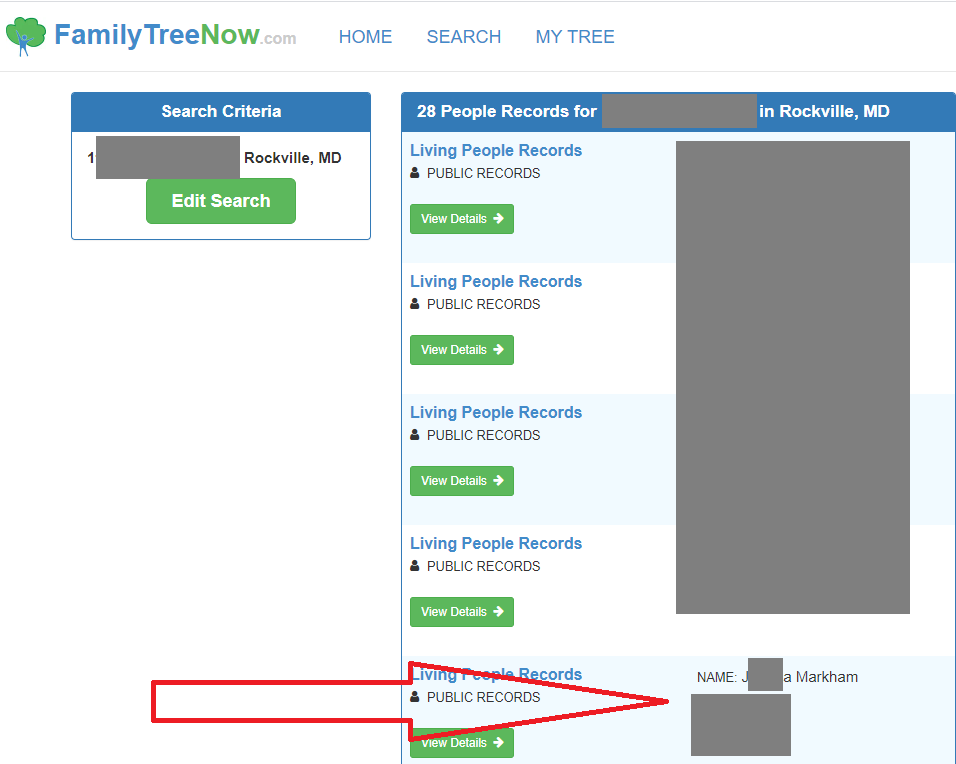
Then we google her and find her linkedin page and where she went to law school, yay!
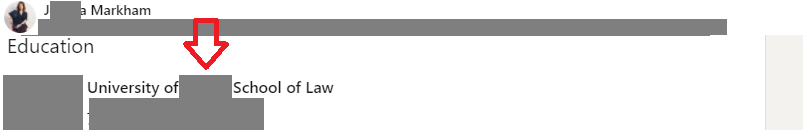
Saved the hardest one for last.. sigh
Good luck
This was definitely the hardest, and only 2 people had solved it by the time I got to start on it (had a meeting that ran for 2 hours right after the presentation). I started with peekyou, tried all sorts of google dorks but couldn’t find him. Then I remembered I found his wife:
So we know j_____a’s name so we find her IG which is public:
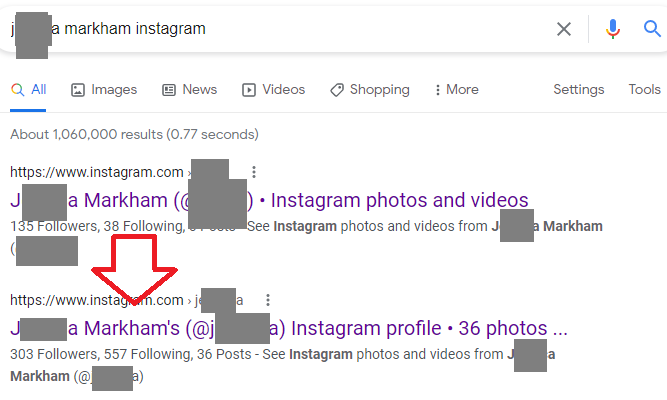
We tried looking through her posts to see if Brian liked any of her photos, of course he did not, so we had to look through the 300+ people she follows to find him, only took me like 15 mins ugh: